Security News

Your humble vulture is a glass-half-empty-and-who-the-hell-drank-my-whiskey kind of bird, so instead of looking on the bright side, we're looking at the two Microsoft bugs that have already been found and exploited by miscreants. The two that are under active exploit, at least according to Microsoft, are CVE-2023-29336, a Win32k elevation of privilege vulnerability; and CVE-2023-24932, a Secure Boot security feature bypass vulnerability, which was exploited by the BlackLotus bootkit to infect Windows machines.

Microsoft is hoping to curb a growing threat to multi-factor authentication by enforcing a number-matching step for those using Microsoft Authenticator push notifications when signing into services. In October 2022, Microsoft introduced number matching as an option, as well as other security features like location and application context, in Microsoft Authenticator.

For May 2023 Patch Tuesday, Microsoft has delivered fixes for 38 CVE-numbered vulnerabilities, including a patch for a Windows bug and a Secure Boot bypass flaw exploited by attackers in the wild. "Historically, we've seen three separate examples where Win32k EoP vulnerabilities were exploited as zero days. In January 2022, Microsoft patched CVE-2022-21882, which was exploited in the wild and is reportedly a patch bypass for CVE-2021-1732, which was patched in February 2021 and also exploited in the wild. In October 2021, Microsoft patched another Win32k EoP, identified as CVE-2021-40449, which was linked to a remote access trojan known as MysterySnail, which was a patch bypass for CVE-2016-3309. However, it is unclear if this flaw is a patch bypass."

Microsoft has released security updates to address a Secure Boot zero-day vulnerability exploited by BlackLotus UEFI malware to infect fully patched Windows systems. According to a Microsoft Security Response Center blog post, the security flaw was used to bypass patches released for CVE-2022-21894, another Secure Boot bug abused in BlackLotus attacks last year.

Microsoft has released security updates to address a Secure Boot zero-day vulnerability exploited by BlackLotus UEFI malware to infect fully patched Windows systems. According to a Microsoft Security Response Center blog post, the security flaw was used to bypass patches released for CVE-2022-21894, another Secure Boot bug abused in BlackLotus attacks last year.

Today is Microsoft's May 2023 Patch Tuesday, and security updates fix three zero-day vulnerabilities and a total of 38 flaws. Today's Patch Tuesday is one of the smallest in terms of resolved vulnerabilities, with only thirty-eight vulnerabilities fixed, not including eleven Microsoft Edge vulnerabilities fixed last week, on May 5th. Three zero-days fixed.

Microsoft has enabled number matching for Microsoft Authenticator push notifications to improve user sign-in security. "If the user has a different default authentication method, there's no change to their default sign-in. If the default method is Authenticator, they get number matching," Microsoft clarified, and noted that users can't opt out of this feature.
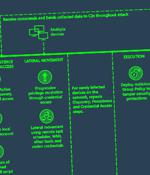
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management software, Microsoft said. The tech giant's threat intelligence team said it observed both Mango Sandstorm and Mint Sandstorm weaponizing CVE-2023-27350 in their operations to achieve initial access.

Microsoft has started enforcing number matching in Microsoft Authenticator push notifications to fend off multi-factor authentication fatigue attacks. As previously announced, Microsoft will start enforcing number matching for Microsoft Authenticator MFA alerts to block MFA fatigue attack attempts across tenants beginning today.

Microsoft says Iranian state-backed hackers have joined the ongoing assault targeting vulnerable PaperCut MF/NG print management servers. "The PaperCut exploitation activity by Mint Sandstorm appears opportunistic, affecting organizations across sectors and geographies," the Microsoft Threat Intelligence team said.