Security News

Discover how ManageEngine Log360, a comprehensive SIEM solution empowers you to prevent internal security breaches, safeguard your network from external threats, protect sensitive data, and ensure...

Reducing costs is the biggest priority for Australian SMEs. Due to increasing costs and higher interest rates in the Australian market, SME leaders were found to be seeking "Growth without additional cost," the report said, in an effort to drive productivity enhancements through technology optimisation rather than through more spending.

State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho ManageEngine and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command revealed on Thursday. CISA was part of the incident response between February and April and said the hacking groups had been in the compromised aviation organization's network since at least January after hacking an Internet-exposed server running Zoho ManageEngine ServiceDesk Plus and a Fortinet firewall.

North Korean state-sponsored hackers Lazarus Group have been exploiting a ManageEngine ServiceDesk vulnerability to target internet backbone infrastructure and healthcare institutions in Europe and the US. The group leveraged the vulnerability to deploy QuiteRAT, downloaded from an IP address previously associated with the Lazarus hacking group. The malware Cisco Talos researchers dubbed QuiteRAT is a simple remote access trojan that's similar to Lazarus Group's MagicRAT malware, only smaller in size.
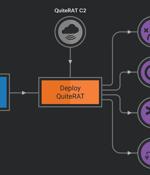
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-part analysis published today. What's more, a closer examination of the adversary's recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT. The fact that the Lazarus Group continues to rely on the same tradecraft despite those components being well-documented over the years underscores the threat actor's confidence in their operations, Talos pointed out.

The North Korean state-backed hacker group tracked as Lazarus has been exploiting a critical vulnerability in Zoho's ManageEngine ServiceDesk to compromise an internet backbone infrastructure provider and healthcare organizations. Cisco Talos researchers observed attacks against UK internet firms in early 2023, when Lazarus leveraged an exploit for CVE-2022-47966, a pre-authentication remote code execution flaw affecting multiple Zoho ManageEngine products.

Multiple threat actors have been observed opportunistically weaponizing a now-patched critical security vulnerability impacting several Zoho ManageEngine products since January 20, 2023. Tracked as CVE-2022-47966, the remote code execution flaw allows a complete takeover of the susceptible systems by unauthenticated attackers.

A critical remote code execution vulnerability affecting multiple Zoho ManageEngine products is now being exploited in attacks. While investigating attacks that led to the compromise of some of its customers' ManageEngine instances, Rapid7 also observed post-exploitation activity.

Proof-of-concept exploit code is now available for a remote code execution vulnerability in multiple Zoho ManageEngine products. The PoC exploit was tested against ServiceDesk Plus and Endpoint Central, and Horizon3 "Expect this POC to work unmodified on many of the ManageEngine products that share some of their codebase with ServiceDesk Plus or EndpointCentral."

If your enterprise is running ManageEngine products that were affected by CVE-2022-47966, check now whether they've been updated to a non-vulnerable version because Horizon3's will be releasing technical details and a PoC exploit this week. CVE-2022-47966 is an unauthenticated remote code execution vulnerability that has been found by a researcher with Viettel Cyber Security in two dozen ManageEngine products, including Access Manager Plus, ADSelfService Plus, Endpoint DLP, Password Manager Pro, PAM360, ServiceDesk Plus, and others.