Security News
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices. First advertised on online hacking forums at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple's Safari browser and the Notes app.

A new Emotet phishing campaign is targeting U.S. taxpayers by impersonating W-9 tax forms allegedly sent by the Internal Revenue Service and companies you work with. Emotet is a notorious malware infection distributed through phishing emails that in the past contained Microsoft Word and Excel documents with malicious macros that install the malware.

A malicious Python package on PyPI uses Unicode as an obfuscation technique to evade detection while stealing and exfiltrating developers' account credentials and other sensitive data from compromised devices. The malicious package, named "Onyxproxy," uses a combination of different Unicode fonts in the source code to help it bypass automated scans and defenses that identify potentially malicious functions based on string matching.

The North Korean advanced persistent threat actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help files to download additional malware. "The group is constantly evolving its tools, techniques, and procedures while experimenting with new file formats and methods to bypass security vendors," Zscaler researchers Sudeep Singh and Naveen Selvan said in a new analysis published Tuesday.

"The packages contained a PowerShell script that would execute upon installation and trigger a download of a 'second stage' payload, which could be remotely executed," JFrog researchers Natan Nehorai and Brian Moussalli said. While NuGet packages have been in the past found to contain vulnerabilities and be abused to propagate phishing links, the development marks the first-ever discovery of packages with malicious code.

A cyber espionage campaign targeting organizations in Russian-occupied regions of Ukraine is using novel malware to steal data, according to Russia-based infosec software vendor Kaspersky. In a report published Tuesday, Kaspersky researchers detailed the infections, which use a PowerShell-based backdoor they've named "PowerMagic" and a previously unknown framework dubbed "CommonMagic" that can steal files from USB devices, take screenshots every three seconds, and send all of this data back to the attacker.
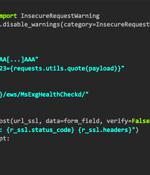
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia. The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "Network-based forms of detection."

Security researchers have discovered attacks from an advanced threat actor that used "a previously unseen malicious framework" called CommonMagic and a new backdoor called PowerMagic. Researchers at cybersecurity company Kaspersky say that the hackers are interested in collecting data from victims in Donetsk, Lugansk, and Crimea.

Poorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different variants of malware called ShellBot. ShellBot is installed on servers that have weak credentials, but only after threat actors make use of scanner malware to identify systems that have SSH port 22 open.
A new piece of malware dubbed dotRunpeX is being used to distribute numerous known malware families such as Agent Tesla, Ave Maria, BitRAT, FormBook, LokiBot, NetWire, Raccoon Stealer, RedLine Stealer, Remcos, Rhadamanthys, and Vidar. "DotRunpeX is a new injector written in.NET using the Process Hollowing technique and used to infect systems with a variety of known malware families," Check Point said in a report published last week.