Security News
A financially-motivated North Korean threat actor is suspected to be behind a new Apple macOS malware strain called RustBucket. The Apple device management company attributed it to a threat actor known as BlueNoroff, a subgroup within the infamous Lazarus cluster that's also tracked under the monikers APT28, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.

VirusTotal announced on Monday the launch of a new artificial intelligence-based code analysis feature named Code Insight.The new feature is powered by the Google Cloud Security AI Workbench introduced at the RSA Conference 2023 and which uses the Sec-PaLM large language model specifically fine-tuned for security use cases.

A new enterprise-targeting malware toolkit called 'Decoy Dog' has been discovered after inspecting anomalous DNS traffic that is distinctive from regular internet activity. Decoy Dog helps threat actors evade standard detection methods through strategic domain aging and DNS query dribbling, aiming to establish a good reputation with security vendors before switching to facilitating cybercrime operations.

Researchers are seeing a rise in attacks spreading the EvilExtractor data theft tool, used to steal users' sensitive data in Europe and the U.S. EvilExtractor is sold by a company named Kodex for $59/month, featuring seven attack modules, including ransomware, credential extraction, and Windows Defender bypassing. While marketed as a legitimate tool, BleepingComputer was told that EvilExtractor is primarily promoted to threat actors on hacking forums.

The enterprise-targeting Bumblebee malware is distributed through Google Ads and SEO poisoning that promote popular software like Zoom, Cisco AnyConnect, ChatGPT, and Citrix Workspace. Bumblebee is a malware loader discovered in April 2022, thought to have been developed by the Conti team as a replacement for the BazarLoader backdoor, used for gaining initial access to networks and conducting ransomware attacks.

Threat groups are on the rise, and Google Cloud's cyberdefense unit Mandiant is tracking 3,500 of them, with 900 added last year, including 265 first identified during Mandiant's investigations in 2022. The study, based on Mandiant Consulting investigations of targeted attack activity between Jan. 1 and Dec. 31, 2022, found an increasing number of new malware families.

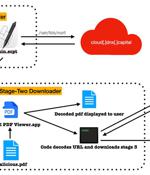
A new Lazarus campaign considered part of "Operation DreamJob" has been discovered targeting Linux users with malware for the first time. Lazarus' Operation DreamJob, also known as Nukesped, is an ongoing operation targeting people who work in software or DeFi platforms with fake job offers on LinkedIn or other social media and communication platforms.

The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users. The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.

The Pakistan-based advanced persistent threat actor known as Transparent Tribe used a two-factor authentication tool used by Indian government agencies as a ruse to deliver a new Linux backdoor called Poseidon. Transparent Tribe is also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, and has a track record of targeting Indian government organizations, military personnel, defense contractors, and educational entities.

The US, UK, and Cisco are warning of Russian state-sponsored APT28 hackers deploying a custom malware named 'Jaguar Tooth' on Cisco IOS routers, allowing unauthenticated access to the device. A joint report released today by the UK National Cyber Security Centre, US Cybersecurity and Infrastructure Security Agency, the NSA, and the FBI details how the APT28 hackers have been exploiting an old SNMP flaw on Cisco IOS routers to deploy a custom malware named 'Jaguar Tooth.