Security News

Samsung has unveiled a new security feature called 'Auto Blocker' as part of the One UI 6 update, offering enhanced malware protection on Galaxy devices. Auto Blocker is an opt-in security feature that prevents the side-loading of risky apps downloaded from outside the Galaxy Store and Google Play.

A new NuGet typosquatting campaign pushes malicious packages that abuse Visual Studio's MSBuild integration to execute code and install malware stealthily. The latest NuGet campaign was spotted by ReversingLabs on October 15, 2023, utilizing different typosquatting packages to install malware.

Cybersecurity researchers have uncovered a new set of malicious packages published to the NuGet package manager using a lesser-known method for malware deployment. Software supply chain security...

A new malware wiper known as BiBi-Linux is being used to destroy data in attacks targeting Linux systems belonging to Israeli companies. The wiper sample discovered by Security Joes also features no obfuscation, packing, or other protective measures, making malware analysts' jobs much easier.

A pro-Hamas hacktivist group has been observed using a new Linux-based wiper malware dubbed BiBi-Linux Wiper, targeting Israeli entities amidst the ongoing Israeli-Hamas war. "This malware is an...

Huawei, Honor, and Vivo smartphones and tablets are displaying strange 'Security threat' alerts urging the deletion of the Google app, warning that it is detected as the 'TrojanSMS-PA' malware. BleepingComputer contacted Google to determine if a recent app update might have caused the sudden uptick in malware warnings, but a spokesperson said Google Play Protect is not triggering the alert.
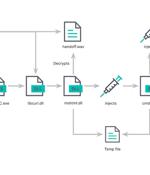
A new cyber attack campaign has been observed using spurious MSIX Windows app package files for popular software such as Google Chrome, Microsoft Edge, Brave, Grammarly, and Cisco Webex to...

The North Korean Lazarus hacking group repeatedly compromised a software vendor using flaws in vulnerable software despite multiple patches and warnings being made available by the developer. SIGNBT can also fetch additional payloads from the C2 and deploy them on the host, providing Lazarus with operational versatility.

Apple pushed several security fixes on Wednesday, including one for all iPhone and iPads used before September last year that has already been exploited by cyber snoops. This is the second patch that Apple has issued to fix the vulnerability.

A sophisticated cross-platform malware platform named StripedFly flew under the radar of cybersecurity researchers for five years, infecting over a million Windows and Linux systems during that time. Kaspersky discovered the true nature of the malicious framework last year, finding evidence of its activity starting in 2017, with the malware wrongly classified as just a Monero cryptocurrency miner.