Security News
A new malware campaign is leveraging a high-severity security flaw in the Popup Builder plugin for WordPress to inject malicious JavaScript code. According to Sucuri, the campaign has infected...

A financially motivated threat actor is using known vulnerabilities to target public-facing services and deliver custom malware to unpatched Windows and Linux systems. Magnet Goblin - as the threat actor has been dubbed by Check Point researchers - has been targeting unpatched edge devices and public-facing servers for years.

Hackers are breaching WordPress sites by exploiting a vulnerability in outdated versions of the Popup Builder plugin, infecting over 3,300 websites with malicious code. Sucuri says the exact actions of the code may vary, but the primary purpose of the injections appears to be redirecting visitors of infected sites to malicious destinations such as phishing pages and malware-dropping sites.

A financially motivated hacking group named Magnet Goblin uses various 1-day vulnerabilities to breach public-facing servers and deploy custom malware on Windows and Linux systems. Check Point analysts who identified Magnet Goblin report that these threat actors are quick to exploit newly disclosed vulnerabilities, in some cases exploiting flaws a day after a PoC exploit is released.

"Our Web-Based PLC malware resides in PLC memory, but ultimately gets executed client-side by various browser-equipped devices throughout the ICS environment. From there, the malware uses ambient browser-based credentials to interact with the PLC's legitimate web APIs to attack the underlying real-world machinery," the researchers explained. "While previous attacks on PLCs infect either the control logic or firmware portions of PLC computation, our proposed malware exclusively infects the web application hosted by the emerging embedded webservers within the PLCs," the researchers noted.

Stolen ChatGPT credentials are a hot commodity on the dark web, according to Singapore-based threat intelligence firm Group-IB, which claims to have found some 225,000 stealer logs containing login details for the service last year. According to Group-IB, it found around 130,000 of the ChatGPT credential-containing logs in the five months from June to October, 2023, representing a 36 percent increase in the number of logs found in the prior five-month period between January and May of last year.
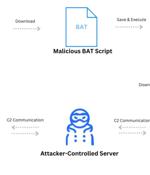
Threat actors have been leveraging fake websites advertising popular video conferencing software such as Google Meet, Skype, and Zoom to deliver a variety of malware targeting both Android and...

Hackers are targeting misconfigured servers running Apache Hadoop YARN, Docker, Confluence, or Redis with new Golang-based malware that automates the discovery and compromise of the hosts. According to the researchers, the hackers deploy a set of four novel Golang payloads that are responsible for identifying and exploiting hosts running services for Hadoop YARN, Docker, Confluence, and Redis.

A new malware dubbed 'WogRAT' targets both Windows and Linux in attacks abusing an online notepad platform named 'aNotepad' as a covert channel for storing and retrieving malicious code. The malware contains encrypted source code for a malware downloader that is compiled and executed on the fly.

North Korean threat actors have exploited the recently disclosed security flaws in ConnectWise ScreenConnect to deploy a new malware called TODDLERSHARK. According to a report shared by Kroll with...