Security News

An analysis of information-stealing malware logs published on the dark web has led to the discovery of thousands of consumers of child sexual abuse material, indicating how such information could be used to combat serious crimes. Distributed via phishing, spam campaigns, cracked software, fake update websites, SEO poisoning, and malvertising, data harvested using such programs typically find their way onto the dark web in the form of stealer logs from where they are purchased by other cybercriminals to further their schemes.
The malware known as GootLoader continues to be in active use by threat actors looking to deliver additional payloads to compromised hosts. "Updates to the GootLoader payload have resulted in...

Over the past six months, there has been a notable surge in Android financial threats - malware targeting victims' mobile banking funds, whether in the form of 'traditional' banking malware or, more recently, cryptostealers, according to ESET. Vidar infostealer targets Windows users. Infostealing malware can now be found impersonating generative AI tools, and new mobile malware GoldPickaxe is capable of stealing facial recognition data to create deepfake videos used by the malware's operators to authenticate fraudulent financial transactions.

Hackers are targeting older versions of the HTTP File Server from Rejetto to drop malware and cryptocurrency mining software. The researchers say that during the attacks the hackers collect information about the system, install backdoors and various other types of malware.

Thousands of pedophiles who download and share child sexual abuse material were identified through information-stealing malware logs leaked on the dark web, highlighting a new dimension of using stolen credentials in law enforcement investigations. Previous analysis has shown that information-stealer logs can contain crucial business account data or credentials to accounts that can expose proprietary information.
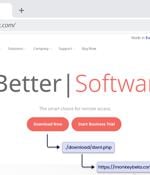
The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader malware families distributed using the drive-by download technique this year, findings from Sekoia...
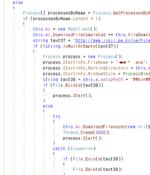
An unnamed South Korean enterprise resource planning (ERP) vendor's product update server has been found to be compromised to deliver a Go-based backdoor dubbed Xctdoor. The AhnLab Security...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day flaw in Cisco NX-OS Software used in its switches to deliver malware. The vulnerability, tracked as...

Cisco has patched an NX-OS zero-day exploited in April attacks to install previously unknown malware as root on vulnerable switches. "The threat actors gathered administrator-level credentials to gain access to Cisco Nexus switches and deploy a previously unknown custom malware that allowed them to remotely connect to compromised devices, upload additional files and execute malicious code."