Security News

A 25-year-old California man pleaded guilty to stealing and dumping 1.1TB of data from the House of Mouse When someone stole more than a terabyte of data from Disney last year, it was believed to...

Russian companies have been targeted as part of a large-scale phishing campaign that's designed to deliver a known malware called DarkWatchman. Targets of the attacks include entities in the...

Cybersecurity researchers have shed light on a Russian-speaking cyber espionage group called Nebulous Mantis that has deployed a remote access trojan called RomCom RAT since mid-2022. RomCom...

Google dumped io_uring after $1M in bug bounties A proof-of-concept program has been released to demonstrate a so-called monitoring "blind spot" in how some Linux antivirus and other endpoint...

In a new campaign detected in March 2025, senior members of the World Uyghur Congress (WUC) living in exile have been targeted by a Windows-based malware that's capable of conducting surveillance....

Who could possibly be behind this attack on an ethnic minority China despises? Researchers at Canada’s Citizen Lab have spotted a phishing campaign and supply chain attack directed at Uyghur...

Sometimes, silence is the best option An Oklahoma City cybersecurity professional accused of installing spyware on a hospital PC confirmed on LinkedIn key details of the drama.…
North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute malware during the fake hiring process. "In this new campaign, the threat actor...

Cybersecurity researchers are warning about a new malware called DslogdRAT that's installed following the exploitation of a now-patched security flaw in Ivanti Connect Secure (ICS). The malware,...
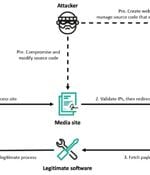
At least six organizations in South Korea have been targeted by the prolific North Korea-linked Lazarus Group as part of a campaign dubbed Operation SyncHole. The activity targeted South Korea's...