Security News

Microsoft has warned of a new wave of CACTUS ransomware attacks that leverage malvertising lures to deploy DanaBot as an initial access vector. The DanaBot infections led to "hands-on-keyboard...

Affiliates of the ALPHV/BlackCat ransomware-as-a-service operation are turning to malvertising campaigns to establish an initial foothold in their victims' systems. The Nitrogen malware campaign was first observed in June, but the tactic of malvertising associated with Nitrogen is new.

A new malvertising campaign has been found to employ fake sites that masquerade as legitimate Windows news portal to propagate a malicious installer for a popular system profiling tool called CPU-Z. "This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix, and VNC Viewer as seen in its infrastructure and cloaking templates used to avoid detection," Malwarebytes' Jérôme Segura said. While malvertising campaigns are known to set up replica sites advertising widely-used software, the latest activity marks a deviation in that the website mimics WindowsReport[.

The popularity of Brazil's PIX instant payment system has made it a lucrative target for threat actors looking to generate illicit profits using a new malware called GoPIX. Kaspersky, which has...

The real impact of the cybersecurity poverty line on small organizationsIn this Help Net Security interview, Brent Deterding, CISO at Afni, delves into the realities and myths surrounding the cybersecurity poverty line, exploring the role of budget, knowledge, and leadership. Cisco IOS XE zero-day exploited by attackers to deliver implantA previously unknown vulnerability affecting networking devices running Cisco IOS XE software is being exploited by a threat actor to take control of the devices and install an implant, Cisco Talos researchers have warned today.
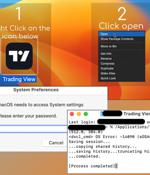
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer, indicating that it's being actively maintained by its author. An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023.
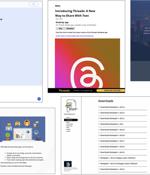
"And with businesses now leveraging the reach of social media for advertising, attackers have a new, highly-lucrative type of attack to add to their arsenal - hijacking business accounts." Cyber attacks targeting Meta Business and Facebook accounts have gained popularity over the past year, courtesy of activity clusters such as Ducktail and NodeStealer that are known to raid businesses and individuals operating on Facebook.

A new malvertising campaign has been observed leveraging ads on Google Search and Bing to target users seeking IT tools like AnyDesk, Cisco AnyConnect VPN, and WinSCP, and trick them into downloading trojanized installers with an aim to breach enterprise networks and likely carry out future ransomware attacks. Dubbed Nitrogen, the "Opportunistic" activity is designed to deploy second-stage attack tools such as Cobalt Strike, Sophos said in a Wednesday analysis.
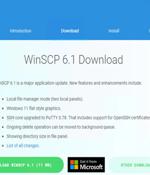
Threat actors associated with the BlackCat ransomware have been observed employing malvertising tricks to distribute rogue installers of the WinSCP file transfer application. "Malicious actors used malvertising to distribute a piece of malware via cloned webpages of legitimate organizations," Trend Micro researchers said in an analysis published last week.

The shift to Google malvertising is the latest example of how crimeware actors are devising alternate delivery routes to distribute malware ever since Microsoft announced plans to block the execution of macros in Office by default from files downloaded from the internet. NET applications for concealing its behavior and are tasked with distributing the FormBook malware family.