Security News

Months of work reveals how this tricky malware family targets... the financial services sector A brand-new macOS malware strain from North Korean state-sponsored hackers has been spotted in the wild.…

The North Korea-linked nation-state group called BlueNoroff has been attributed to a previously undocumented macOS malware strain dubbed ObjCShellz. Jamf Threat Labs, which disclosed details of the malware, said it's used as part of the RustBucket malware campaign, which came to light earlier this year.

North Korean hackers are using novel MacOS malware named KandyKorn to target blockchain engineers of a cryptocurrency exchange platform. By impersonating blockchain engineering community members on Discord, the attackers used social engineering techniques to make victims download a malicious ZIP file.

A new macOS malware dubbed 'KandyKorn' has been spotted in a campaign attributed to the North Korean Lazarus hacking group, targeting blockchain engineers of a cryptocurrency exchange platform. At the final stage of the attack, a loader known as HLoader is used, which impersonates Discord and uses macOS binary code-signing techniques seen in past Lazarus campaigns.

State-sponsored threat actors from the Democratic People's Republic of Korea (DPRK) have been found targeting blockchain engineers of an unnamed crypto exchange platform via Discord with a novel...

The vulnerability, which the researchers named iLeakage, enables threat actors to read Gmail messages, reveal passwords and uncover other personal information. The iLeakage vulnerability has not yet been exploited in the wild as of October 27.

Apple has released yet another round of security patches to address three actively exploited zero-day flaws impacting iOS, iPadOS, macOS, watchOS, and Safari, taking the total tally of zero-day...

Regular tune-ups help protect Macs, both desktop and laptop models, from potential data loss, needlessly slow performance and other issues. Just what steps should a macOS tune-up checklist include? Check out the steps below, from TechRepublic Premium, to ensure you get proper, consistent results during each macOS tune-up.
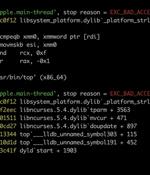
A set of memory corruption flaws have been discovered in the ncurses programming library that could be exploited by threat actors to run malicious code on vulnerable Linux and macOS systems. "Using environment variable poisoning, attackers could chain these vulnerabilities to elevate privileges and run code in the targeted program's context or perform other malicious actions," Microsoft Threat Intelligence researchers Jonathan Bar Or, Emanuele Cozzi, and Michael Pearse said in a technical report published today.

Enterprise macOS users are being targeted by attackers slinging new information-stealing malware dubbed MetaStealer. Dmg - and the inclusion of words such as "Official Brief Description" indicate that the malware peddlers are going specifically after enterprise macOS users.