Security News

Issuing and installing SSL certificates doesn't have to be a challenge, especially when there are tools like acme. Installing SSL certificates isn't difficult, but it's a process every Linux administrator will have to take on at some point in their career.

Kali Linux 2021.3 released: Kali NetHunter on a smartwatch, wider OpenSSL compatibility, new tools, and more!Offensive Security has released Kali Linux 2021.3, the latest version of its popular open source penetration testing platform. Third-party cloud providers: Expanding the attack surfaceIn this interview with Help Net Security, Fred Kneip, CEO at CyberGRX, talks about the lack of visibility into third-party risk, how to address this issue, and what companies should consider when choosing the right cloud provider.
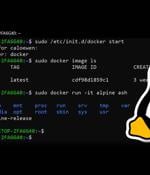
Linux binaries have been found trying to take over Windows systems in what appears to be the first publicly identified malware to utilize Microsoft's Windows Subsystem for Linux to install unwelcome payloads. On Thursday, Black Lotus Labs, the threat research group at networking biz Lumen Technologies, said it had spotted several malicious Python files compiled in the Linux binary format ELF for Debian Linux.
Microsoft on Tuesday addressed a quartet of security flaws as part of its Patch Tuesday updates that could be abused by adversaries to target Azure cloud customers and elevate privileges as well as allow for remote takeover of vulnerable systems. The list of flaws, collectively called OMIGOD by researchers from Wiz, affect a little-known software agent called Open Management Infrastructure that's automatically deployed in many Azure services -.

Manual updates required for existing Azure VMs. While working to address these bugs, Microsoft introduced an Enhanced Security commit on August 11, exposing all the details a threat actor would need to create an OMIGOD exploit. Automatic updates disabled: manually update extension using instructions here Azure Automation State Configuration, DSC Extension On Premises.

A number of malicious samples have been created for the Windows Subsystem for Linux with the goal of compromising Windows machines, highlighting a sneaky method that allows the operators to stay under the radar and thwart detection by popular anti-malware engines. "These files acted as loaders running a payload that was either embedded within the sample or retrieved from a remote server and was then injected into a running process using Windows API calls," researchers from Lumen Black Lotus Labs said in a report published on Thursday.

Security researchers have discovered malicious Linux binaries created for the Windows Subsystem for Linux, indicating that hackers are trying out new methods to compromise Windows machines. The next step is to inject the malware into a running process using Windows API calls, a technique that is neither new nor sophisticated.

Microsoft has addressed four critical vulnerabilities collectively known as OMIGOD, found in the Open Management Infrastructure software agent silently installed on Azure Linux machines accounting for more than half of Azure instances. OMI is a software service for IT management with support for most UNIX systems and modern Linux platforms, used by multiple Azure services, including Open Management Suite, Azure Insights, Azure Automation.

Kali Linux 2021.3 was released yesterday by Offensive Security and includes a new set of tools, improved virtualization support, and a new OpenSSL configuration that increases the attack surface. Kali Linux is a Linux distribution designed for cybersecurity professionals and ethical hackers to perform penetration testing and security audits.

Offensive Security has released Kali Linux 2021.3, the latest version of its popular open source penetration testing platform. OpenSSL has been configured for wider compatibility, allowing the use of legacy protocols, meaning that Kali can now talk to older, legacy systems that use them.