Security News

Offensive Security has released Kali Linux 2022.3, the third version of 2022, with virtual machine improvements, Linux Kernel 5.18.5, new tools to play with, and improved ARM support. With this release, Kali Linux is using Linux Kernel 5.18.5.

The bug fixes for iPhones and iPads include remote code execution flaws in components from the kernel itself to Apple's image rendering library, graphics drivers, video processing modules and more. Several of these bugs warn that "a malicious application may be able to execute arbitrary code with kernel privileges".

NVIDIA has published the source code of its Linux kernel modules for the R515 driver, allowing developers to provide greater integration, stability, and security for Linux distributions. The products supported by these drivers include all models built on the Turing and Ampere architecture, released after 2018, including the GeForce 30 and GeForce 20 series, the GTX 1650 and 1660, and data center-grade A series, Tesla, and Quadro RTX. According to the GPU maker, this is a step toward improving its products' experience on the Linux platform, simplifying the integration process in Linux distributions, debugging, and boosting contribution activity.

Google has released the second part of the May security patch for Android, including a fix for an actively exploited Linux kernel vulnerability. As Android uses a modified Linux kernel, the vulnerability also affects the operating system.

Max Kellermann, a coder and security researcher for German content management software creators CM4all, has just published a fascinating report about a Linux kernel bug that was patched recently. He called the vulnerability Dirty Pipe, because it involves insecure interaction between a true Linux file and a Linux pipe, which is a memory-only data buffer that can be used like a file.

Linux distributions are in the process of issuing patches to address a newly disclosed security vulnerability in the kernel that could allow an attacker to overwrite arbitrary data into any read-only files and allow for a complete takeover of affected systems. The Linux kernel flaw is said to have existed since version 5.8, with the vulnerability sharing similarities to that of Dirty Cow, which came to light in October 2016.

To go along with the "Dirty Pipe" Linux security bug coming to light, two researchers from Huawei - Yiqi Sun and Kevin Wang - have discovered a vulnerability in the "Control groups" feature of the Linux kernel which allows attackers to escape containers, escalate privileges and execute arbitrary commands on a host machine. The bug exists in the Linux kernel's "Cgroup release agent write" feature, which is found in the "Kernel/cgroup/cgroup-v1.c" function.

A Linux local privilege escalation flaw dubbed Dirty Pipe has been discovered and disclosed along with proof-of-concept exploit code. Max Kellermann said he found the programming blunder and reported it to the kernel security team in February, which issued patches within a few days.
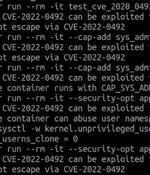
Details have emerged about a now-patched high-severity vulnerability in the Linux kernel that could potentially be abused to escape a container in order to execute arbitrary commands on the container host. The shortcoming resides in a Linux kernel feature called control groups, also referred to as cgroups version 1, which allows processes to be organized into hierarchical groups, effectively making it possible to limit and monitor the usage of resources such as CPU, memory, disk I/O, and network.

Google says it bumped up rewards for reports of Linux Kernel, Kubernetes, Google Kubernetes Engine, or kCTF vulnerabilities by adding bigger bonuses for zero-day bugs and exploits using unique exploitation techniques. "We increased our rewards because we recognized that in order to attract the attention of the community we needed to match our rewards to their expectations," Google Vulnerability Matchmaker Eduardo Vela explained.