Security News

More than 11,500 Juniper Networks devices are exposed to a new remote code execution vulnerability, and infosec researchers are pressing admins to urgently apply the patches. It's somewhat of a repeat scenario for Juniper Networks, which only recently got done patching the last round of critical RCE bugs in Junos OS, which runs on SRX firewalls and EX switches.

Juniper Networks has fixed a critical pre-authentication remote code execution vulnerability in Junos OS on SRX firewalls and EX switches.CVE-2024-21591 is an out-of-bounds write vulnerability that could allow an unauthenticated, network-based threat actor to carry out a denial-of service attack, an RCE attack, or gain root privileges on exposed devices.

Juniper Networks has released updates to fix a critical remote code execution (RCE) vulnerability in its SRX Series firewalls and EX Series switches. The issue, tracked as CVE-2024-21591, is rated...

Juniper Networks has released security updates to fix a critical pre-auth remote code execution vulnerability in its SRX Series firewalls and EX Series switches. CISA also warned in November of a Juniper pre-auth RCE exploit used in the wild, chaining four bugs tracked as CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, and CVE-2023-36847 and impacted the company's SRX firewalls and EX switches.

Collaborative strategies are key to enhanced ICS securityIn this Help Net Security interview, Marko Gulan, Cyber Security Consultant at Schneider Electric, discusses the complexities of safeguarding industrial control systems. Modeling organizations' defensive mechanisms with MITRE D3FENDFunded by the National Security Agency, MITRE's D3FEND framework is helping to provide standardization, specificity, and repeatability needed by cybersecurity engineers.

CISA has ordered US federal agencies to patch five vulnerabilities used by attackers to compromise Juniper networking devices, and to do so by Friday. Juniper Networks fixed four flaws affecting the J-Web GUI of Junos OS-powered devices in late August 2023, and urged customers to update their SRX firewalls and EX switches to plug the security holes.

The U.S. Cybersecurity and Infrastructure Security Agency has given a November 17, 2023, deadline for federal agencies and organizations to apply mitigations to secure against a number of security flaws in Juniper Junos OS that came to light in August. The agency on Monday added five vulnerabilities to the Known Exploited Vulnerabilities catalog, based on evidence of active exploitation -.

CISA warned federal agencies today to secure Juniper devices on their networks by Friday against four vulnerabilities now used in remote code execution attacks as part of a pre-auth exploit chain. The alert comes one week after Juniper updated its advisory to notify customers that the flaws found in Juniper's J-Web interface have been successfully exploited in the wild.
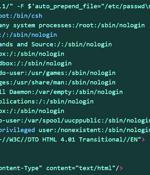
New research has found that close to 12,000 internet-exposed Juniper firewall devices are vulnerable to a recently disclosed remote code execution flaw. VulnCheck, which discovered a new exploit for CVE-2023-36845, said it could be exploited by an "Unauthenticated and remote attacker to execute arbitrary code on Juniper firewalls without creating a file on the system."

About 79 percent of public-facing Juniper SRX firewalls remain vulnerable to a single security flaw can allow an unauthenticated attacker to remotely execute code on the devices, according to threat intelligence platform provider VulnCheck. Juniper revealed and addressed five flaws, which affect all versions of Junos OS on SRX firewalls and EX Series switches, in an out-of-cycle security bulletin on August 17.