Security News

The video is really amazing. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered.

An Active! Mail zero-day remote code execution vulnerability is actively exploited in attacks on large organizations in Japan. [...]

Japanese telecommunication services provider NTT Communications Corporation (NTT) is warning almost 18,000 corporate customers that their information was compromised during a cybersecurity incident. [...]
The China-linked threat actor known as Winnti has been attributed to a new campaign dubbed RevivalStone that targeted Japanese companies in the manufacturing, materials, and energy sectors in...

The National Police Agency (NPA) and the Cabinet Cyber Security Center in Japan have linked a cyber-espionage campaign targeting the country to the Chinese state-backed "MirrorFace" hacking group. [...]

‘MirrorFace’ group found ways to run malware in the Windows sandbox, which is worrying Japan’s National Police Agency and Center of Incident Readiness and Strategy for Cybersecurity have confirmed...

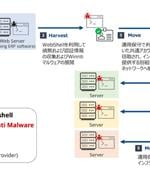
Japanese organizations are the target of a Chinese nation-state threat actor that leverages malware families like LODEINFO and NOOPDOOR to harvest sensitive information from compromised hosts while stealthily remaining under the radar in some cases for a time period ranging from two to three years. "The actors behind NOOPDOOR not only utilized LODEINFO during the campaign, but also utilized the new backdoor to exfiltrate data from compromised enterprise networks," it said.

The Japanese Space Exploration Agency discovered it was under attack using zero-day exploits while working with Microsoft to probe a 2023 cyberattack on its systems. Then there's the mention of zero-day attacks in the last sentence of a section about countermeasures like closer network monitoring and improve remote access security the agency adopted.
Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Japanese police placed fake payment cards in convenience stores to protect the elderly targeted by tech support scams or unpaid money fraud. The cards are labeled "Virus Trojan Horse Removal Payment Card" and "Unpaid Bill Late Fee Payment Card," and were created by the Echizen Police in the Fukui prefecture in Japan as an alert mechanism.