Security News

Microsoft has discovered that an Iranian hacking group known as 'Mint Sandstorm' is conducting cyberattacks on US critical infrastructure in what is believed to be retaliation for recent attacks on Iran's infrastructure. In a new report, researchers in Microsoft's Threat Intelligence team explain that a subgroup of Mint Sandstorm switched from performing surveillance in 2022 to performing direct attacks on US critical infrastructure.

The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems. While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022.

US Cyber Command operators have confirmed they carried out an online defensive mission in Albania, in response to last year's cyber attacks against the local government. Over the course of the three-month deployment, Cyber National Mission Force troops worked with their Albanian counterparts to hunt for cyber threats and identify vulnerabilities on networks in the NATO country.

"Notably the targets in this instance were all women who are actively involved in political affairs and human rights in the Middle East region," Secureworks Counter Threat Unit said in a report shared with The Hacker News. Another bespoke malware linked to the group is a C++-based Telegram "Grabber" tool that facilitates data harvesting on a large scale from Telegram accounts after obtaining the target's credentials.

An Iranian nation-state group sanctioned by the U.S. government has been attributed to the hack of the French satirical magazine Charlie Hebdo in early January 2023. Two Iranian nationals have been accused for their role in the disinformation and threat campaign.
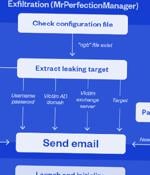
The Iranian nation-state hacking group known as OilRig has continued to target government organizations in the Middle East as part of a cyber espionage campaign that leverages a new backdoor to exfiltrate data. "The campaign abuses legitimate but compromised email accounts to send stolen data to external mail accounts controlled by the attackers," Trend Micro researchers Mohamed Fahmy, Sherif Magdy, and Mahmoud Zohdy said.

The U.K. National Cyber Security Centre on Thursday warned of spear-phishing attacks mounted by Russian and Iranian state-sponsored actors for information-gathering operations. The activity is typical of spear-phishing campaigns, where the threat actors send messages tailored to the targets, while also taking enough time to research their interests and identify their social and professional circles.

The U.K. National Cyber Security Centre has issued a warning of Russian and Iranian state-sponsored hackers increasingly targeting organizations and individuals. More specifically, the country's cybersecurity agency has identified a spike in spear-phishing attacks attributed to threat actors tracked as SEABORGIUM and TA453.

The threat actor known as BackdoorDiplomacy has been linked to a new wave of attacks targeting Iranian government entities between July and late December 2022. Palo Alto Networks Unit 42, which is tracking the activity under its constellation-themed moniker Playful Taurus, said it observed the government domains attempting to connect to malware infrastructure previously identified as associated with the adversary.

Groups tied to the Russian intelligence services will also continue to target geographic neighbors with disinformation campaigns, intelligence gathering, and possibly low-level disruptive attacks. Traditional espionage targets will continue to be a focus; for example, we saw evidence in August 2022 of Russian intelligence services using spear phishing emails to target staff at the Argonne and Brookhaven national laboratories in the US, which conduct cutting edge energy research.