Security News

According to Etay Maor, Senior Director Security Strategy at Cato Networks, "It's interesting to note critical infrastructure doesn't necessarily have to be power plants or electricity. A nation's monetary system or even a global monetary system can be and should be considered a critical infrastructure as well." Not to mention the infamous Colonial Pipeline attack, which has become the poster child of critical infrastructure attacks.

Devices used in critical infrastructure are riddled with vulnerabilities that can cause denial of service, allow configuration manipulation, and achieve remote code execution, according to security researchers. Most of these operational technology products - which include industrial control systems and related devices - claim security certifications, some of which they did not actually have.

The Federal Bureau of Investigation revealed in its 2022 Internet Crime Report that ransomware gangs breached the networks of at least 860 critical infrastructure organizations last year. "The IC3 received 870 complaints that indicated organizations belonging to a critical infrastructure sector were victims of a ransomware attack," the FBI said.

Today, the U.S. Cybersecurity & Infrastructure Security Agency announced a new pilot program to help critical infrastructure entities protect their information systems from ransomware attacks. "Through the Ransomware Vulnerability Warning Pilot, which started on January 30, 2023, CISA is undertaking a new effort to warn critical infrastructure entities that their systems have exposed vulnerabilities that may be exploited by ransomware threat actors," the cybersecurity agency said.

Today, the U.S. Cybersecurity & Infrastructure Security Agency announced a new pilot program to help critical infrastructure entities protect their information systems from ransomware attacks. "Recognizing the persistent threat posed by ransomware attacks to organizations of all sizes, the Cybersecurity and Infrastructure Security Agency announces today the establishment of the Ransomware Vulnerability Warning Pilot," the cybersecurity agency said.

An international law enforcement operation involving the FBI and police agencies worldwide led to the arrest of the suspected administrator of the NetWire remote access trojan and the seizure of the service's web domain and hosting server. Since at least 2014, NetWire has been a tool of choice in various malicious activities, including phishing attacks, BEC campaigns, and to breach corporate networks.

Veeam urged customers to patch a high-severity Backup Service security vulnerability impacting its Backup & Replication software.The flaw was reported in mid-February by a security researcher known as Shanigen, and it affects all Veeam Backup & Replication versions.
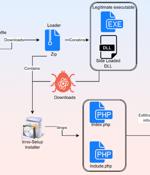
Cybersecurity researchers have discovered a new information stealer dubbed SYS01stealer targeting critical government infrastructure employees, manufacturing companies, and other sectors. "The threat actors behind the campaign are targeting Facebook business accounts by using Google ads and fake Facebook profiles that promote things like games, adult content, and cracked software, etc. to lure victims into downloading a malicious file," Morphisec said in a report shared with The Hacker News.
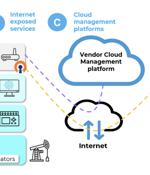
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things devices from four different vendors that could pose a significant attack surface for threat actors looking to exploit operational technology environments."Threat actors can exploit vulnerabilities in Wireless IIoT devices to gain initial access to internal OT networks," Israeli industrial cybersecurity company Otorio said.

Protecting CNI is a difficult task, thanks to a combination of a lack of skilled professionals, legacy systems and a lack of security investment that leaves them open to attack. While one would assume that these systems should run the latest and greatest security measures, due to their sensitive nature, many of these systems operate on legacy machines that can't be reset and can't be patched.