Security News
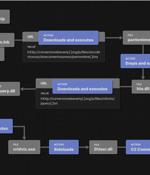
The suspected Pakistan-aligned threat actor known as SideCopy has been observed leveraging themes related to the Indian military research organization as part of an ongoing phishing campaign. Interestingly, the same attack chains have been observed to load and execute Action RAT as well as an open source remote access trojan known as AllaKore RAT. The latest infection sequence documented by Fortinet is no different, leading to the deployment of an unspecified strain of RAT that's capable of communicating with a remote server and launching additional payloads.

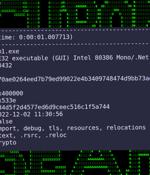
The Pakistan-based advanced persistent threat actor known as Transparent Tribe used a two-factor authentication tool used by Indian government agencies as a ruse to deliver a new Linux backdoor called Poseidon. Transparent Tribe is also tracked as APT36, Operation C-Major, PROJECTM, and Mythic Leopard, and has a track record of targeting Indian government organizations, military personnel, defense contractors, and educational entities.

The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in attacks targeting the Indian education sector using a continuously maintained piece of malware called Crimson RAT. While the suspected Pakistan-based threat group is known to target military and government entities in the country, the activities have since expanded to include the education vertical. Last month, ESET attributed Transparent Tribe to a cyber espionage campaign aimed at infecting Indian and Pakistani Android users with a backdoor called CapraRAT. An analysis of Crimson RAT samples has revealed the presence of the word "Wibemax," corroborating a previous report from Fortinet.

The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021. The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report shared with The Hacker News.

A spear-phishing campaign targeting Indian government entities aims to deploy an updated version of a backdoor called ReverseRAT. Cybersecurity firm ThreatMon attributed the activity to a threat actor tracked as SideCopy. SideCopy is a threat group of Pakistani origin that shares overlaps with another actor called Transparent Tribe.
A new targeted phishing campaign has zoomed in on a two-factor authentication solution called Kavach that's used by Indian government officials. LNK files are used to initiate code execution which eventually downloads and runs a malicious C# payload, which functions as a remote access trojan," Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a new report.

The Indian government on Friday released a draft version of the much-awaited data protection regulation, making it the fourth such effort since it was first proposed in July 2018. The Digital Personal Data Protection Bill, 2022, as it's called, aims to secure personal data, while also seeking users' consent in what the draft claims is "Clear and plain language" describing the exact kinds of information that will be collected and for what purpose.
Cybersecurity researchers are warning of "Massive phishing campaigns" that distribute five different malware targeting banking users in India. "The bank customers targeted include account subscribers of seven banks, including some of the most well-known banks located in the country and potentially affecting millions of customers," Trend Micro said in a report published this week.

The Transparent Tribe threat actor has been linked to a new campaign aimed at Indian government organizations with trojanized versions of a two-factor authentication solution called Kavach. The cybersecurity company said the advanced persistent threat group has also conducted low-volume credential harvesting attacks in which rogue websites masquerading as official Indian government websites were set up to lure unwitting users into entering their passwords.
Asia In Brief India's government has given itself the power to compel social networks to take down content. India's minister of state for electronics and information technology, Rajeev Chandrasekhar, said the GACs are needed because India's previous attempt at regulating social media - requiring the networks to appoint a grievance officer - has not delivered.