Security News

Microsoft on Friday shared more of the tactics, techniques, and procedures adopted by the Russia-based Gamaredon hacking group to facilitate a barrage of cyber espionage attacks aimed at several entities in Ukraine over the past six months. The attacks are said to have singled out government, military, non-government organizations, judiciary, law enforcement, and non-profit organizations with the main goal of exfiltrating sensitive information, maintaining access, and leveraging it to move laterally into related organizations.

Symantec finds evidence of continued Russian hacking campaigns in Ukraine. Security researchers at Symantec have presented what they said is further evidence that the Russian advanced persistent threat hacking team known as Shuckworm has been actively waging a cyber espionage campaign against organizations in Ukraine.

The Iranian-backed MuddyWater hacking group is conducting a new malicious campaign targeting private Turkish organizations and governmental institutions. The hacking group has been attributed to attacks against entities in Central and Southwest Asia and numerous public and privately-held organizations from Europe, Asia, and North America in the telecommunications, government, oil, and airline industry sectors.
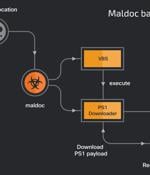
Details have emerged about a previously undocumented malware campaign undertaken by the Iranian MuddyWater advanced persistent threat group targeting Turkish private organizations and governmental institutions. "This campaign utilizes malicious PDFs, XLS files and Windows executables to deploy malicious PowerShell-based downloaders acting as initial footholds into the target's enterprise," Cisco Talos researchers Asheer Malhotra and Vitor Ventura said in a newly published report.
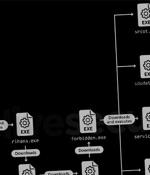
A threat actor with potential links to an Indian cybersecurity company has been nothing if remarkably persistent in its attacks against military organizations based in South Asia, including Bangladesh, Nepal, and Sri Lanka, since at least September 2020 by deploying different variants of its bespoke malware framework. Slovak cybersecurity firm ESET attributed the highly targeted attack to a hacking group known as Donot Team.

VirusTotal, the popular online service for analyzing suspicious files, URLs and IP addresses, can be used to collect credentials stolen by malware, researchers at SafeBreach have found. With a €600 VirusTotal license, they have managed to collect more than 1,000,000 credentials just by executing simple searches with a few tools.

A new ransomware family called 'White Rabbit' appeared in the wild recently, and according to recent research findings, could be a side-operation of the FIN8 hacking group. The first public mention of the White Rabbit ransomware was in a tweet by ransomware expert Michael Gillespie, seeking a sample of the malware.

The U.S. Cyber Command on Wednesday officially confirmed MuddyWater's ties to the Iranian intelligence apparatus, while simultaneously detailing the various tools and tactics adopted by the espionage actor to burrow into victim networks. "MuddyWater has been seen using a variety of techniques to maintain access to victim networks," USCYBERCOM's Cyber National Mission Force said in a statement.

US Cyber Command has officially linked the Iranian-backed MuddyWatter hacking group to Iran's Ministry of Intelligence and Security. MOIS is the Iran government's leading intelligence agency, tasked with coordinating the country's intelligence and counterintelligence, as well as covert actions supporting the Islamic regime's goals beyond Iran's borders.

Trojanized installers of the Telegram messaging application are being used to distribute the Windows-based Purple Fox backdoor on compromised systems. First discovered in 2018, Purple Fox comes with rootkit capabilities that allow the malware to be planted beyond the reach of security solutions and evade detection.