Security News

The North Korean advanced persistent threat group known as Kimsuky has been observed using a piece of custom malware called RandomQuery as part of a reconnaissance and information exfiltration operation. "Lately, Kimsuky has been consistently distributing custom malware as part of reconnaissance campaigns to enable subsequent attacks," SentinelOne researchers Aleksandar Milenkoski and Tom Hegel said in a report published today.

A financially motivated cybercriminal group known as FIN7 resurfaced last month, with Microsoft threat analysts linking it to attacks where the end goal was the deployment of Clop ransomware payloads on victims' networks. "The group was observed deploying the Clop ransomware in opportunistic attacks in April 2023, its first ransomware campaign since late 2021.".

Hackers are now actively probing for vulnerable Essential Addons for Elementor plugin versions on thousands of WordPress websites in massive Internet scans, attempting to exploit a critical account password reset flaw disclosed earlier in the month. The critical-severity flaw is tracked as CVE-2023-32243 and impacts Essential Addons for Elementor versions 5.4.0 to 5.7.1, allowing unauthenticated attackers to arbitrarily reset the passwords of administrator accounts and assume control of the websites.

Cybersecurity researchers have unearthed previously undocumented attack infrastructure used by the prolific state-sponsored group SideWinder to strike entities located in Pakistan and China. SideWinder has been known to be active since at least 2012, with attack chains primarily leveraging spear-phishing as an intrusion mechanism to obtain a foothold into targeted environments.

A financially motivated cybergang tracked by Mandiant as 'UNC3944' is using phishing and SIM swapping attacks to hijack Microsoft Azure admin accounts and gain access to virtual machines. From there, the attackers abuse the Azure Serial Console to install remote management software for persistence and abuse Azure Extensions for stealthy surveillance.

The backdoor malware is deployed in a custom and malicious firmware designed specifically for TP-Link routers so that the hackers can launch attacks appearing to originate from residential networks. While Check Point has not determined how the attackers infect TP-Link routers with the malicious firmware image, they said it could be by exploiting a vulnerability or brute-forcing the administrator's credentials.
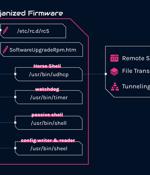
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023. An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.
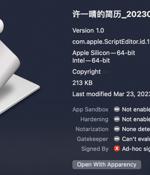
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems. Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.

Hackers are actively exploiting a recently fixed vulnerability in the WordPress Advanced Custom Fields plugin roughly 24 hours after a proof-of-concept exploit was made public. The vulnerability in question is CVE-2023-30777, a high-severity reflected cross-site scripting flaw that allows unauthenticated attackers to steal sensitive information and escalate their privileges on impacted WordPress sites.

Senators Mark Warner and Susan Collins this week introduced an amendment to the Help America Vote Act that would require the nation's Election Assistance Commission to include penetration testing in its certification process of voting hardware and software. That tech would need to undergo pen testing before it could be used in elections.