Security News

The attack utilizes the legitimate file-syncing software SyncThing in combination with malware called SPECTR. Vermin's apparent motive is to steal sensitive information from military organizations. SyncThing establishes a peer-to-peer connection for data synchronization, which is used for stealing documents and account passwords.

Chinese shopping platform Pandabuy told BleepingComputer it previously paid a a ransom demand to prevent stolen data from being leaked, only for the same threat actor to extort the company again this week. On March 31, 2024, a threat actor using the alias 'Sanggiero' published 3 million rows of data stolen from PandaBuy on BreachForums, exposing customer names, phone numbers, email addresses, login IP addresses, home addresses, and order details.

Threat actors are increasingly abusing legitimate and commercially available packer software such as BoxedApp to evade detection and distribute malware such as remote access trojans and...

Cybersecurity researchers have discovered a malicious Python package uploaded to the Python Package Index (PyPI) repository that's designed to deliver an information stealer called Lumma (aka...
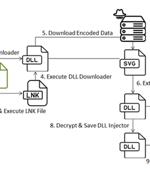
A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per...

The North Korea-linked threat actor known as Andariel has been observed using a new Golang-based backdoor called Dora RAT in its attacks targeting educational institutes, manufacturing firms, and...

AI platform Hugging Face says that its Spaces platform was breached, allowing hackers to access authentication secrets for its members. Hugging Face Spaces is a repository of AI apps created and submitted by the community's users, allowing other members to demo them.

Japanese crypto exchange DMM Bitcoin is warning that 4,502.9 Bitcoin, or approximately $308 million, has been stolen from one of its wallets today, making it the most significant cryptocurrency heist of 2024. "At approximately 1:26 p.m. on Friday, May 31, 2024, we detected an unauthorized leak of Bitcoin from our wallet," DMM Bitcoin told customers.
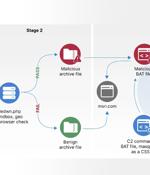
The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages. APT28,...

A never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting individuals and organizations in the software and information...