Security News

Almost 2.7 billion records of personal information for people in the United States were leaked on a hacking forum, exposing names, social security numbers, all known physical addresses, and...
Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users. Successful exploitation of one of these flaws could allow a remote attacker to obtain covert audio capture from Sonos devices by means of an over-the-air attack.

Critical 1Password flaws may allow hackers to snatch your passwords (CVE-2024-42219, CVE-2024-42218)
Two vulnerabilities affecting the macOS version of the popular 1Password password manager could allow malware to steal secrets stored in the software's vaults and obtain the account unlock key, AgileBits has confirmed. Discovered by the Robinhood Red Team during a security assessment of 1Password for Mac and then privately reported to the software's makers, the vulnerabilities have been fixed in two consecutive versions of the software: v8.10.36 and v8.10.38.

The U.S. Cybersecurity and Infrastructure Security Agency has disclosed that threat actors are abusing the legacy Cisco Smart Install feature with the aim of accessing sensitive data. The agency said it has seen adversaries "Acquire system configuration files by leveraging available protocols or software on devices, such as abusing the legacy Cisco Smart Install feature."

CISA recommends disabling the legacy Cisco Smart Install feature after seeing it abused by threat actors in recent attacks to steal sensitive data, such as system configuration files. [...]

Gambling blockchain Ronin Network suffered a security incident yesterday when white hat hackers exploited an undocumented vulnerability on the Ronin bridge to withdraw 4,000 ETH and 2 million...

Cybersecurity researchers have disclosed details of security flaws in the Roundcube webmail software that could be exploited to execute malicious JavaScript in a victim's web browser and steal sensitive information from their account under specific circumstances. "When a victim views a malicious email in Roundcube sent by an attacker, the attacker can execute arbitrary JavaScript in the victim's browser," cybersecurity company Sonar said in an analysis published this week.

A hacker has breached Mobile Guardian, a digital classroom management platform used worldwide, and remotely wiped data from at least 13,000 student's iPads and Chromebooks. [...]

Criminals increasingly deploy stolen credentials to gain initial access to user accounts, bringing new demands for security. Credentials can also be guessed through approaches like brute force attacks, where cybercriminals deploy tools that test password combinations continuously until they discover the right one.
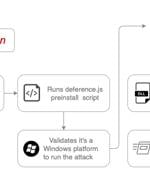
The North Korea-linked threat actor known as Moonstone Sleet has continued to push malicious npm packages to the JavaScript package registry with the aim of infecting Windows systems, underscoring the persistent nature of their campaigns. The security arm of the cloud monitoring firm is tracking the threat actor under the name Stressed Pungsan, which exhibits overlaps with a newly discovered North Korean malicious activity cluster dubbed Moonstone Sleet.