Security News

Midnight Blizzard – a cyber espionage group that has been linked to the Russian Foreign Intelligence Service (SVR) – is targeting government, academia, defense, and NGO workers with phishing...
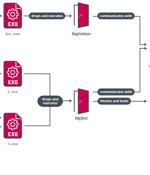
A government entity and a religious organization in Taiwan were the target of a China-linked threat actor known as Evasive Panda that infected them with a previously undocumented post-compromise...

The FBI and the U.S. Cybersecurity & Infrastructure Security Agency (CISA) have disclosed that Chinese hackers breached commercial telecommunication service providers in the United States. [...]

The fourth day of Pwn2Own Ireland 2024 marked the end of the hacking competition with more than $1 million in prizes for over 70 unique zero-day vulnerabilities in fully patched devices. [...]

The infamous cryptojacking group known as TeamTNT appears to be readying for a new large-scale campaign targeting cloud-native environments for mining cryptocurrencies and renting out breached...

The North Korean Lazarus hacking group exploited a Google Chrome zero-day tracked as CVE-2024-4947 through a fake decentralized finance (DeFi) game targeting individuals in the cryptocurrency space. [...]

On the first day of Pwn2Own Ireland, participants demonstrated 52 zero-day vulnerabilities across a range of devices, earning a total of $486,250 in cash prizes. [...]

AI adoption and integration has continued its rapid momentum within the hacking community, according to Bugcrowd. Nevertheless, it continues to pose both benefits and unfortunate cyber risks. This...

Threat actors have been exploiting a vulnerability in the Roundcube Webmail client to target government organizations in the Commonwealth of Independent States (CIS) region, the successor of the...

The prolific Chinese nation-state actor known as APT41 (aka Brass Typhoon, Earth Baku, Wicked Panda, or Winnti) has been attributed to a sophisticated cyber attack targeting the gambling and...