Security News

Ukrainian national Mark Sokolovsky was sentenced to 60 months in federal prison for one count of conspiracy to commit computer intrusion. According to court documents, he conspired to operate the...

The Russian hacking group tracked as APT29 (aka "Midnight Blizzard") is using a network of 193 remote desktop protocol proxy servers to perform man-in-the-middle (MiTM) attacks to steal data and...

The Russia-linked APT29 threat actor has been observed repurposing a legitimate red teaming attack methodology as part of cyber attacks leveraging malicious Remote Desktop Protocol (RDP)...
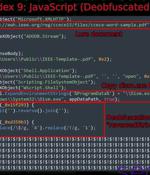
A new phishing campaign has been observed employing tax-themed lures to deliver a stealthy backdoor payload as part of attacks targeting Pakistan. Cybersecurity company Securonix, which is...
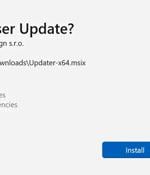
Bogus software update lures are being used by threat actors to deliver a new stealer malware called CoinLurker. "Written in Go, CoinLurker employs cutting-edge obfuscation and anti-analysis...

The Chinese Winnti hacking group is using a new PHP backdoor named 'Glutton' in attacks on organizations in China and the U.S., and also in attacks on other cybercriminals. [...]

A threat actor tracked as MUT-1244 has stolen over 390,000 WordPress credentials in a large-scale, year-long campaign targeting other threat actors using a trojanized WordPress credentials checker. [...]

Russian cyber-espionage group Turla, aka "Secret Blizzard," is utilizing other threat actors' infrastructure to target Ukrainian military devices connected via Starlink. [...]

Russian cyber-espionage group Turla, aka "Secret Blizzard," is utilizing other threat actors' infrastructure to target Ukrainian military devices connected via Starlink. [...]

The U.S. government on Tuesday unsealed charges against a Chinese national for allegedly breaking into thousands of Sophos firewall devices globally in 2020. Guan Tianfeng (aka gbigmao and...