Security News

Sasi says that an attacker first needs to convince the victim to make a call to a number that starts with a Man Machine Interface code that the mobile carrier set up to enable call forwarding. "First, you receive a call from the attacker who will convince you to make a call to the following number **67* or *405*. Within a few minutes, your WhatsApp would be logged out, and the attackers would get complete control of your account" - Rahul Sasi.

Chinese-linked threat actors are now actively exploiting a Microsoft Office zero-day vulnerability to execute malicious code remotely on Windows systems. This Microsoft Windows Support Diagnostic Tool remote code execution flaw impacts all Windows client and server platforms still receiving security updates.

An "Aggressive" advanced persistent threat group known as SideWinder has been linked to over 1,000 new attacks since April 2020. "Some of the main characteristics of this threat actor that make it stand out among the others, are the sheer number, high frequency and persistence of their attacks and the large collection of encrypted and obfuscated malicious components used in their operations," cybersecurity firm Kaspersky said in a report that was presented at Black Hat Asia this month.

The gathered credentials are then exfiltrated and sold on Russian cybercrime forums for prices ranging from a few to thousands of U.S. dollars. Armed with this login information, the agency pointed out, adversaries can proceed to conduct brute-force credential stuffing attacks to break into victim accounts spanning different accounts, internet sites, and services.

Cybercriminals are offering to sell for thousands of U.S. dollars network access credentials for higher education institutions based in the United States. The sensitive information consists of network credentials and virtual private network access "To a multitude" of higher education organizations in the U.S. In some cases, the seller posted a screenshot proving that the credentials provide the advertised access.
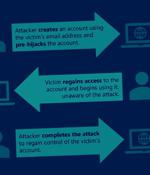
Malicious actors can gain unauthorized access to users' online accounts via a new technique called "Account pre-hijacking," new research has found. The attack takes aim at the account creation process that's ubiquitous in websites and other online platforms, enabling an adversary to perform a set of actions before an unsuspecting victim creates an account in a target service.
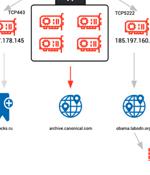
Cybersecurity researchers are calling attention to a free-to-use browser automation framework that's being increasingly used by threat actors as part of their attack campaigns. The U.S. cybersecurity company said it observed command-and-control IP addresses associated with malware such as Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft, the maker of the Browser Automation Studio.

The Versus Market, one of the most popular English-speaking criminal darknet markets, is shutting down after discovering a severe exploit that could have allowed access to its database and exposed the IP address of its servers. Apparently, after finding these vulnerabilities, the operators of Versus have decided to pull the plug themselves, finding it too risky to continue.

The hacker behind this hijack has now broken silence and explained his reasons to BleepingComputer. The hijacker of these libraries is an Istanbul-based security researcher, Yunus Aydın aka SockPuppets, who has attested to the fact when approached by BleepingComputer.

Yesterday, developers took notice of two hugely popular Python and PHP libraries, respectively, 'ctx' and 'PHPass' that had been hijacked, as first reported in the news by BleepingComputer. According to the hacker, rather "Security researcher," this was a bug bounty exercise and no malicious activity was intended.