Security News

Threat analysts have uncovered a new campaign attributed to APT37, a North Korean group of hackers, targeting high-value organizations in the Czech Republic, Poland, and other European countries. In this campaign, the hackers use malware known as Konni, a remote access trojan capable of establishing persistence and performing privilege escalation on the host.

Twitter has suffered a data breach after threat actors used a vulnerability to build a database of phone numbers and email addresses belonging to 5.4 million accounts, with the data now up for sale on a hacker forum for $30,000. "Hello, today I present you data collected on multiple users who use Twitter via a vulnerability.," reads the forums post selling the Twitter data.

On Thursday, Ukrainian media group TAVR Media confirmed that it was hacked to spread fake news about President Zelenskiy being in critical condition and under intensive care. SSSCIP added that the attackers breached TAVR Media's servers and broadcasting systems to spread fake news suggesting that the Ukrainian President is allegedly under intensive care, in critical condition, with Parliament Chairman Ruslan Stefanchuk acting in his stead. Zelenskyi also refuted the reports in a video shared on his official Instagram account, saying they were fake news spread by Russian-linked threat actors.

A large software development company whose software is used by different state entities in Ukraine was at the receiving end of an "Uncommon" piece of malware, new research has found. The malware, first observed on the morning of May 19, 2022, is a custom variant of the open source backdoor known as GoMet and is designed for maintaining persistent access to the network.

Dubbed Atlas Intelligence Group, the cybergang has been spotted by security researchers recruiting independent black-hat hackers to execute specific aspects of its own campaigns. The threat group markets services that include data leaks, distributed denial of service, remote desktop protocol hijacking and additional network penetration services, according to a Thursday report by threat intelligence firm Cyberint.

The advanced persistent threat actor tracked as Evilnum is once again exhibiting signs of renewed activity aimed at European financial and investment entities. "Evilnum is a backdoor that can be used for data theft or to load additional payloads," enterprise security firm Proofpoint said in a report shared with The Hacker News.

A threat actor is promoting a new version of their free-to-use 'Redeemer' ransomware builder on hacker forums, offering unskilled threat actors an easy entry to the world of encryption-backed extortion attacks. Unlike many Ransomware-as-a-Service operations, anyone can download and use the Redeemer ransomware builder to launch their own attacks.
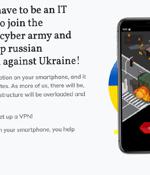
Russian threat actors capitalized on the ongoing conflict against Ukraine to distribute Android malware camouflaged as an app for pro-Ukrainian hacktivists to launch distributed denial-of-service attacks against Russian sites. "The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the actor and disseminated via links on third party messaging services."
Six vulnerabilities in the MiCODUS MV720 GPS tracker that's used by organizations around the world to manage and protect vehicle fleets could be exploited by attackers to remotely cut fuel to or abruptly stop vehicles. The MiCODUS MV720 is a hardwired GPS tracker through which fleet owners can track vehicles, cut off fuel to them, geofence them so they can't be driven outside specific areas, and generally have remote control over the vehicles.
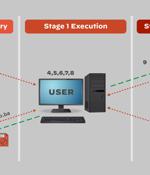
The Russian state-sponsored hacking collective known as APT29 has been attributed to a new phishing campaign that takes advantage of legitimate cloud services like Google Drive and Dropbox to deliver malicious payloads on compromised systems. What's changed in the newer iterations is the use of cloud services like Dropbox and Google Drive to conceal their actions and retrieve additional malware into target environments.