Security News

Hackers have exploited a zero-day vulnerability in General Bytes Bitcoin ATM servers to steal cryptocurrency from customers. General Bytes is the manufacturer of Bitcoin ATMs that, depending on the product, allow people to purchase or sell over 40 different cryptocurrencies.

The U.S. Cybersecurity and Infrastructure Security Agency has added seven vulnerabilities to its list of bugs actively exploited by hackers, with the new flaws disclosed by Apple. The 'Known Exploited Vulnerabilities Catalog' is a list of vulnerabilities shared by CISA that are known to be actively exploited in cyberattacks and must be patched by Federal Civilian Executive Branch agencies.

The state-backed Russian cyberespionage group Cozy Bear has been particularly prolific in 2022, targeting Microsoft 365 accounts in NATO countries and attempting to access foreign policy information. Mandiant, who has been tracking the activities of Cozy Bear, reports that the Russian hackers have been vigorously targeting Microsoft 365 accounts in espionage campaigns.

The Donot Team threat actor has updated its Jaca Windows malware toolkit with improved capabilities, including a revamped stealer module designed to plunder information from Google Chrome and Mozilla Firefox browsers. The latest findings from Morphisec build on a prior report from cybersecurity company ESET, which detailed the adversary's intrusions against military organizations based in South Asia using several versions of its yty malware framework, one of which is Jaca.
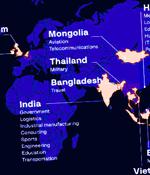
The Chinese advanced persistent threat actor tracked as Winnti has targeted at least 13 organizations geographically spanning across the U.S, Taiwan, India, Vietnam, and China against the backdrop of four different campaigns in 2021. APT41, also known as Barium, Bronze Atlas, Double Dragon, Wicked Panda, or Winnti, is a prolific Chinese cyber threat group that's known to carry out state-sponsored espionage activity in parallel with financially motivated operations at least since 2007.

A Chinese state-sponsored threat activity group named RedAlpha has been attributed to a multi-year mass credential theft campaign aimed at global humanitarian, think tank, and government organizations. The adversary's consistent targeting of think tanks and humanitarian organizations over the past three years falls in line with the strategic interests of the Chinese government, the report added.

The Chinese Winnti hacking group, also known as 'APT41' or 'Wicked Spider,' targeted at least 80 organizations last year and successfully breached the networks of at least thirteen. One of Wintti's unique deployment methods for the Cobalt Strike beacons involved obfuscating the payload on the host to evade detection by software.

The Chinese Winnti hacking group, also known as 'APT41' or 'Wicked Spider,' targeted at least 80 organizations last year and successfully breached the networks of at least thirteen. One of Wintti's unique deployment methods for the Cobalt Strike beacons involved obfuscating the payload on the host to evade detection by software.

The malware loader known as Bumblebee is being increasingly co-opted by threat actors associated with BazarLoader, TrickBot, and IcedID in their campaigns to breach target networks for post-exploitation activities. "Bumblebee operators conduct intensive reconnaissance activities and redirect the output of executed commands to files for exfiltration," Cybereason researchers Meroujan Antonyan and Alon Laufer said in a technical write-up.

The North Korea-backed Lazarus Group has been observed targeting job seekers with malware capable of executing on Apple Macs with Intel and M1 chipsets. Slovak cybersecurity firm ESET linked it to a campaign dubbed "Operation In(ter)ception" that was first disclosed in June 2020 and involved using social engineering tactics to trick employees working in the aerospace and military sectors into opening decoy job offer documents.