Security News

The threat actors behind IcedID malware phishing campaigns are utilizing a wide variety of distribution methods, likely to determine what works best against different targets. The IcedID malware started in 2017 as a modular banking trojan but has since evolved into a malware dropper that is commonly used to gain initial access to corporate networks.

The pro-Russian hacktivist group 'KillNet' is claiming large-scale distributed denial-of-service attacks against websites of several major airports in the U.S., making them unaccessible.The DDoS attacks have overwhelmed the servers hosting these sites with garbage requests, making it impossible for travelers to connect and get updates about their scheduled flights or book airport services.

The pro-Russian hacktivist group 'KillNet' has carried out large-scale DDoS attacks against several U.S. airports' websites, taking many of them offline. The DDoS attacks have overwhelmed the servers hosting these sites with garbage requests, making it impossible for travelers to connect and get updates about their scheduled flights or book airport services.

BNB Chain, a blockchain linked to the Binance cryptocurrency exchange, disclosed an exploit on a cross-chain bridge that drained around $100 million in digital assets. According to Binance CEO Changpeng Zhao, the exploit on the cross-chain bridge "Resulted in extra BNB," prompting a temporary suspension of the Binance Smart Chain.

A severe remote code execution vulnerability in Zimbra's enterprise collaboration software and email platform is being actively exploited, with no patch currently available to remediate the issue. While a fix is yet to be released, Zimbra is urging users to install the "Pax" utility and restart the Zimbra services.

Hackers are actively exploiting an unpatched remote code execution vulnerability in Zimbra Collaboration Suite, a widely deployed web client and email server. Zimbra released a security advisory on September 14 to warn system administrators to install Pax, a portable archiving utility, and restart their Zimbra servers to replace cpio, which is the vulnerable component.

The 'LofyGang' threat actors have created a credential-stealing enterprise by distributing 200 malicious packages and fake hacking tools on code hosting platforms, such as NPM and GitHub. LofyGang is motivated by financial profit, aiming to achieve high-volume account compromise and then resell access to those accounts on various private channels on the dark web, hacking forums, and Discord.
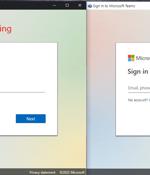
In what's a new phishing technique, it has been demonstrated that the Application Mode feature in Chromium-based web browsers can be abused to create "Realistic desktop phishing applications." Application Mode is designed to offer native-like experiences in a manner that causes the website to be launched in a separate browser window, while also displaying the website's favicon and hiding the address bar.

Three US national security agencies - CISA, the FBI and the NSA - on Thursday issued a joint advisory naming the 20 infosec exploited by state-sponsored Chinese threat actors since 2020. The Cybersecurity and Infrastructure Security Agency, National Security Agency and Federal Bureau of Investigation stated they collectively consider the People's Republic of China state-sponsored cyber activities as "Being one of the largest and most dynamic threats to U.S. government and civilian networks."

Hackers have reportedly stolen 2 million Binance Coins, worth $566 million, from the Binance Bridge.Details are scant at the moment, but the attack appears to have started at 2:30 PM EST today, with the attacker's wallet receiving two transactions [1, 2], each consisting of 1,000,000 BNB. Soon after the hacker began spreading some of the funds across a variety of liquidity pools, attempting to transfer the BNB into other assets.