Security News

The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a decade-old malware to deliver its own reconnaissance and backdoor tools to targets in Ukraine. Google-owned Mandiant, which is tracking the operation under the uncategorized cluster moniker UNC4210, said the hijacked servers correspond to a variant of a commodity malware called ANDROMEDA that was uploaded to VirusTotal in 2013.

A South Africa-based threat actor known as Automated Libra has been observed employing CAPTCHA bypass techniques to create GitHub accounts in a programmatic fashion as part of a freejacking campaign dubbed PURPLEURCHIN. The group "Primarily targets cloud platforms offering limited-time trials of cloud resources in order to perform their crypto mining operations," Palo Alto Networks Unit 42 researchers William Gamazo and Nathaniel Quist said. PURPLEURCHIN first came to light in October 2022 when Sysdig disclosed that the adversary created as many as 30 GitHub accounts, 2,000 Heroku accounts, and 900 Buddy accounts to scale its operation.

To address these challenges, Google, Microsoft and Proton, whose Proton Mail service was a first-mover in secure email, both moved to expand end-to-end encryption offerings. Google's announcement followed that of Proton, an encrypted cloud storage platform launched in 2013 in Geneva, Switzerland by CEO Andy Yen.

A financially motivated threat actor tracked as Blind Eagle has resurfaced with a refined toolset and an elaborate infection chain as part of its attacks targeting organizations in Colombia and Ecuador. Also tracked under the name APT-C-36, Blind Eagle is notable for its narrow geographical focus and launching indiscriminate attacks against South American nations since at least 2018.

According to Palo Alto Networks Unit 42, the threat actors use a new CAPTCHA solving system, follow a more aggressive use of CPU resources for mining, and mixe 'freejacking' with the "Play and Run" technique to abuse free cloud resources. Whereas Sysdig identified 3,200 malicious accounts belonging to 'PurpleUrchin,' Unit 42 now reports that the threat actor has created and used over 130,000 accounts on the platforms since August 2019, when the first signs of its activities can be traced.

A signed Windows driver has been used in attacks on banks in French-speaking countries, likely from a threat actor that stole more than $11 million from various banks. Symantec's report adds some technical details, such as the use of the GuLoader tool for loading malware and a signed driver that helps the attacker kill processes for security products running on the victim network.

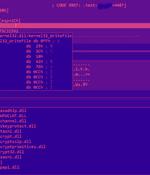
Hackers are abusing the Windows Problem Reporting error reporting tool for Windows to load malware into a compromised system's memory using a DLL sideloading technique. The use of this Windows executable is to stealthy infect devices without raising any alarms on the breached system by launching the malware through a legitimate Windows executable.
A new malware campaign has been observed using sensitive information stolen from a bank as a lure in phishing emails to drop a remote access trojan called BitRAT. The unknown adversary is believed to have hijacked the IT infrastructure of a Colombian cooperative bank, using the information to craft convincing decoy messages to lure victims into opening suspicious Excel attachments. The leaked details include Cédula numbers, email addresses, phone numbers, customer names, payment records, salary details, and addresses, among others.

Now according to Cisco Talos, advanced persistent threat actors and commodity malware families alike are increasingly using Excel add-in files as an initial intrusion vector. One such method turns out to be XLL files, which is described by Microsoft as a "Type of dynamic link library file that can only be opened by Excel."

BlueNoroff, a subcluster of the notorious Lazarus Group, has been observed adopting new techniques into its playbook that enable it to bypass Windows Mark of the Web protections. "BlueNoroff created numerous fake domains impersonating venture capital companies and banks," security researcher Seongsu Park said, adding the new attack procedure was flagged in its telemetry in September 2022.