Security News

Two malicious packages discovered on the npm package registry have been found to leverage GitHub to store Base64-encrypted SSH keys stolen from developer systems on which they were installed. The...

GitHub has revealed that it has rotated some keys in response to a security vulnerability that could be potentially exploited to gain access to credentials within a production container. The...

GitHub rotated keys potentially exposed by a vulnerability patched in December that could let attackers access credentials within production containers via environment variables. "On December 26, 2023, GitHub received a report through our Bug Bounty Program demonstrating a vulnerability which, if exploited, allowed access to credentials within a production container. We fixed this vulnerability on GitHub.com the same day and began rotating all potentially exposed credential," said Github VP and Deputy Chief Security Officer Jacob DePriest.

In a report published on Thursday, security shop Recorded Future warns that GitHub's infrastructure is frequently abused by criminals to support and deliver malware. GitHub domains are seldom blocked by corporate networks, making it a reliable hosting site for malware.

The ubiquity of GitHub in information technology (IT) environments has made it a lucrative choice for threat actors to host and deliver malicious payloads and act as dead drop resolvers,...

In emails sent to GitHub users on Christmas Eve, the company warned that all users contributing code on GitHub.com must enable 2FA by January 19th, 2024. "On January 19th, 2024 at 00:00 your account will be required to have 2FA for authentication. If you have not yet enrolled by that date, your ability to access GitHub.com will be limited until you finish the enrollment process," the company noted in an email to its users.
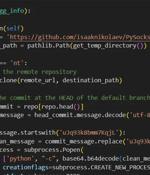
Threat actors are increasingly making use of GitHub for malicious purposes through novel methods, including abusing secret Gists and issuing malicious commands via git commit messages. "Malware...
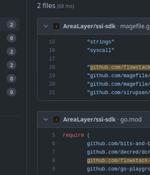
New research has found that over 15,000 Go module repositories on GitHub are vulnerable to an attack called repojacking. "More than 9,000 repositories are vulnerable to repojacking due to GitHub...

GitHub Advanced Security gains AI features, and GitHub Copilot now includes a chatbot option. At the GitHub Universe conference held in San Francisco and virtually on Nov. 8 and Nov. 9, 2023, the company revealed its new open source trends report as well as changes to GitHub Copilot and AI enhancements for GitHub Advanced Security.

In the active Elektra-Leak campaign, attackers hunt for Amazon IAM credentials within public GitHub repositories before using them for cryptomining. New research from Palo Alto Networks's Unit 42 exposes an active attack campaign in which a threat actor hunts for Amazon IAM credentials in real time in GitHub repositories and starts using them less than five minutes later.