Security News

German law enforcement has announced the disruption of a dark web platform called Kingdom Market that specialized in the sales of narcotics and malware to "tens of thousands of users."...

The Federal Criminal Police Office in Germany and the internet-crime combating unit of Frankfurt have announced the seizure of Kingdom Market, a dark web marketplace for drugs, cybercrime tools, and fake government IDs. The law enforcement operation also included authorities from the United States, Switzerland, Moldova, and Ukraine, while one of the administrators has been arrested in the US. Kingdom Market was an English-speaking marketplace on the dark web with international reach that has operated since March 2021.
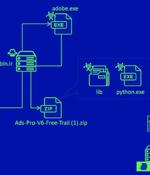
A phishing campaign has been observed delivering an information stealer malware called MrAnon Stealer to unsuspecting victims via seemingly benign booking-themed PDF lures. "This malware is a...

The German Federal Financial Supervisory Authority announced today that an ongoing distributed denial-of-service attack has been impacting its website since Friday. BaFin is Germany's financial regulatory authority, part of the Federal Ministry of Finance, responsible for supervising 2,700 banks, 800 financial, and 700 insurance service providers.
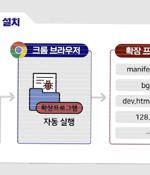
German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The intrusions are designed to strike "Experts on the Korean Peninsula and North Korea issues" through spear-phishing campaigns, the agencies noted.

Remember the Who Targets Me browser extension from privacy activists at Noyb? The group yesterday filed explosive complaints based on log records from the extension that claim six of Germany's political parties broke European data law when they targeted voters on Facebook's adtech platform. The group is claiming the allegedly GDPR-busting activity took place during the country's 2021 federal elections, and filed six complaints yesterday with the Berlin and Bavarian data protection watchdogs against parties spanning the entire German political spectrum.

Europe's proposed "Chat Control" legislation to automatically scan chat, email, and instant message communications for child sexual exploitation material ran up against broad resistance at a meeting of the German Parliament's Digital Affairs Committee on Wednesday. Chat Control 2.0 would make content scanning mandatory, even for encrypted communications - which would mean either content scanning prior to encryption or encryption keys managed by the service provider instead of the end user.

A series of distributed denial-of-service attacks shut down seven German airports' websites on Thursday, a day after a major IT glitch at Lufthansa grounded flights. Ralph Beisel, the general manager of Germany's ADV airport association, confirmed the network-flooding events in an emailed statement to The Register, but did not specify which airports were hit.

A previously unknown threat actor has been targeting companies in the U.S. and Germany with bespoke malware designed to steal confidential information. The attachments range from macro-laced Microsoft Publisher files to PDFs with URLs pointing to JavaScript files.

Google users don't have enough choice over whether - and to what extent - they agree to "Far-reaching processing of their data across services," Germany's competition regulator says, adding that the tech giant should change its "Data processing" terms and practices. They should also be allowed to "Limit the processing of data to the specific service used" and "Be able to differentiate between the purposes for which the data are processed," it said.