Security News

Although many financial institutions are aware of the need for API security to support their new corporate reality, they do not really know how to approach it and especially with which tools. In the API security domain, financial organizations are looking for tools that handle the whole lifecycle.

Russia may ramp up ransomware attacks against the United States as a way to avoid sanctions levied against the nation and Vladimir Putin's government for its invasion of Ukraine, U.S. federal authorities are warning. The Financial Crimes Enforcement Network issued a FinCEN Alert on Wednesday advising all financial institutions to remain vigilant against potential efforts to evade the expansive sanctions and other U.S.-imposed restrictions related to the current conflict.

New Xenomorph Android malware targets more than 50 banking and financial applications. Figure B. The Alien malware has more overall capabilities than Xenomorph, which is far more targeted at stealing banking information.

State-sponsored attackers from China conducted a two-month campaign against Taiwanese financial services firms, according to CyCraft, a security consultancy from the island nation. CyCraft's analysis of the incident alleges that the attack run started in November 2021, when the malicious actors - named as Chinese gang APT10 - used supply chain attacks to target software used by Taiwanese financial institutions.

Financial services leaders cite increased future revenues and improved future profitability as leading reasons to deploy cloud technologies, according to a financial services study by Capco. The report identifies the key trends and opportunities ahead and offer insights to allow financial services institutions to become cloud leaders.
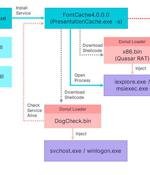
An advanced persistent threat group operating with objectives aligned with the Chinese government has been linked to an organized supply chain attack on Taiwan's financial sector. The second wave of attacks hit a peak between February 10 and 13, 2022, according to a new report published by Taiwanese cybersecurity firm CyCraft, which said the wide-ranging supply chain compromise specifically targeted the software systems of financial institutions, resulting in "Abnormal cases of placing orders."

Social media as a threat channel saw a two-fold increase in attacks throughout 2021, according to a report from PhishLabs. In Q4 and throughout 2021, PhishLabs analysed hundreds of thousands of phishing and social media attacks targeting enterprises, their employees, and brands.

Among its findings, the research reports that despite a community reckoning to ban ransomware activity from online forums, hacker groups used alternate personas to continue to proliferate the use of ransomware against an increasing spectrum of sectors - hitting the financial, utilities and retail sectors most often, accounting for nearly 60% of ransomware detections. "While we ended 2021 focused on a resurgent pandemic and the revelations around the Log4j vulnerability, our third-quarter deep dive into cyber threat activity found notable new tools and tactics among ransomware groups and advanced global threat actors," said Raj Samani, Chief Scientist and Fellow at Trellix.

A Chinese advanced persistent threat group has been targeting Taiwanese financial institutions as part of a "Persistent campaign" that lasted for at least 18 months. The intrusions, whose primary intent was espionage, resulted in the deployment of a backdoor called xPack, granting the adversary extensive control over compromised machines, Broadcom-owned Symantec said in a report published last week.

Another week, another big economy restricting cryptocurrency. In the tweet below, Wimboh Santoso, commissioner of Indonesia's financial services authority the Otoritas Jasa Keuangan, states that the agency has prohibited financial service institutions from using, marketing, and/or facilitating crypto asset trading.