Security News

The notorious cybercrime group known as FIN7 has been observed deploying Cl0p ransomware, marking the threat actor's first ransomware campaign since late 2021. "They then use OpenSSH and Impacket to move laterally and deploy Clop ransomware."

A financially motivated cybercriminal group known as FIN7 resurfaced last month, with Microsoft threat analysts linking it to attacks where the end goal was the deployment of Clop ransomware payloads on victims' networks. "The group was observed deploying the Clop ransomware in opportunistic attacks in April 2023, its first ransomware campaign since late 2021.".

Ex-Conti ransomware members have teamed up with the FIN7 threat actors to distribute a new malware family named 'Domino' in attacks on corporate networks. Domino is a relatively new malware family consisting of two components, a backdoor named 'Domino Backdoor,' which in turn drops a 'Domino Loader' that injects an info-stealing malware DLL into the memory of another process.
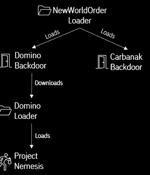
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.

FIN7 is a threat actor that mostly focuses on stealing financial information, but it also sells sensitive information stolen from companies. FIN7 started using ransomware in 2020, being affiliates of a few of the most active ransomware groups: Sodinokibi, REvil, LockBit and DarkSide.

An exhaustive analysis of FIN7 has unmasked the cybercrime syndicate's organizational hierarchy, alongside unraveling its role as an affiliate for mounting ransomware attacks. The highly active threat group, also known as Carbanak, is known for employing an extensive arsenal of tools and tactics to expand its "Cybercrime horizons," including adding ransomware to its playbook and setting up fake security companies to lure researchers into conducting ransomware attacks under the guise of penetration testing.

The notorious FIN7 hacking group uses an automated attack system that exploits Microsoft Exchange and SQL injection vulnerabilities to breach corporate networks, steal data, and select targets for ransomware attacks based on financial size. Next, FIN7's internal 'marketing' team scrutinizes new entries and adds comments on the Checkmarks platform to list victims' current revenue, number of employees, domain, headquarters details, and other information that helps pentesters determine if the firm is worth the time and effort of a ransomware attack.

A new analysis of tools put to use by the Black Basta ransomware operation has identified ties between the threat actor and the FIN7 group. This link "Could suggest either that Black Basta and FIN7 maintain a special relationship or that one or more individuals belong to both groups," cybersecurity firm SentinelOne said in a technical write-up shared with The Hacker News.

Security researchers at Sentinel Labs have uncovered evidence that links the Black Basta ransomware gang to the financially motivated hacking group FIN7, also known as "Carbanak." When analyzing tools used by the ransomware gang in attacks, the researchers found signs that a developer for FIN7 has also authored the EDR evasion tools used exclusively by Black Basta since June 2022.

FIN7 hacking group returns with new methods and members, what should you look out for? A report from Mandiant details the resurfacing of the FIN7 hacking group and the collective's use of new hacking tools along with an expanding roster of attackers.