Security News


The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning that it has observed threat actors leveraging unencrypted persistent cookies managed by the F5 BIG-IP Local Traffic...

The hybrid multicloud strategies that many Australian enterprises have adopted over the last decade could be made more complex by new AI applications. The only solutions could be rationalisation...

A group of suspected Chinese cyberespionage actors named 'Velvet Ant' are deploying custom malware on F5 BIG-IP appliances to gain a persistent connection to the internal network and steal data. Using the compromised F5 BIG-IP devices, the threat actors could stealthily steal sensitive customer and financial information from the company for three years without being detected.

A suspected China-nexus cyber espionage actor has been attributed as behind a prolonged attack against an unnamed organization located in East Asia for a period of about three years, with the...

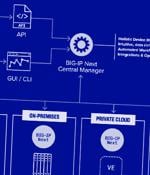
Eclypsium researchers have published details and PoC exploits for two remotely exploitable injection vulnerabilities affecting F5's BIG-IP Next Central Manager. BIG-IP Next Central Manager allows users to centrally control their BIG-IP Next instances and services.
Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator...

F5 has fixed two high-severity BIG-IP Next Central Manager vulnerabilities, which can be exploited to gain admin control and create hidden rogue accounts on any managed assets.Next Central Manager allows administrators to control on-premises or cloud BIG-IP Next instances and services via a unified management user interface.

Considering the ever-changing state of cybersecurity, it's never too late to ask yourself, "am I doing what's necessary to keep my organization's web applications secure?" The continuous evolution...

Crew may well be working under contract for Beijing Chinese spies exploited a couple of critical-severity bugs in F5 and ConnectWise equipment earlier this year to sell access to compromised US...