Security News

On the first day of Pwn2Own Ireland, participants demonstrated 52 zero-day vulnerabilities across a range of devices, earning a total of $486,250 in cash prizes. [...]

Proof-of-concept exploit code is now public for a vulnerability in Microsoft's Remote Registry client that could be used to take control of a Windows domain by downgrading the security of the...

Threat actors have been exploiting a vulnerability in the Roundcube Webmail client to target government organizations in the Commonwealth of Independent States (CIS) region, the successor of the...

Like keeping your camera and microphone private? Patch up In revealing details about a vulnerability that threatens the privacy of Apple fans, Microsoft urges all macOS users to update their systems.…

Unknown threat actors have been observed attempting to exploit a now-patched security flaw in the open-source Roundcube webmail software as part of a phishing attack designed to steal user...

The North Korean threat actor known as ScarCruft has been linked to the zero-day exploitation of a now-patched security flaw in Windows to infect devices with malware known as RokRAT. The...

In this Help Net Security interview, Ismael Valenzuela, Vice President of Threat Research & Intelligence at BlackBerry, discusses the impact of geopolitical tensions on the frequency and...

Cybersecurity researchers have found that entry points could be abused across multiple programming ecosystems like PyPI, npm, Ruby Gems, NuGet, Dart Pub, and Rust Crates to stage software supply...

The Iranian state-sponsored hacking group APT34, aka OilRig, has recently escalated its activities with new campaigns targeting government and critical infrastructure entities in the United Arab...
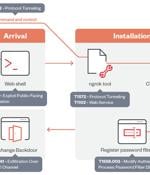
The Iranian threat actor known as OilRig has been observed exploiting a now-patched privilege escalation flaw impacting the Windows Kernel as part of a cyber espionage campaign targeting the...