Security News

There’s been a notable shift in the types of threats targeting software developers, with a total of 17,954 open source malware packages identified in Q1 2025, according to Sonatype. Quarterly...

A previously undocumented threat actor called CeranaKeeper has been linked to a string of data exfiltration attacks targeting Southeast Asia. Slovak cybersecurity firm ESET, which observed...

A new Rust-based information stealer malware called Fickle Stealer has been observed being delivered via multiple attack chains with the goal of harvesting sensitive information from compromised...

Varonis Threat Labs researchers have uncovered two techniques attackers can use can use for covert data and file exfiltration from companies' SharePoint server. "These techniques can bypass the detection and enforcement policies of traditional tools, such as cloud access security brokers, data loss prevention, and SIEMs, by hiding downloads as less suspicious access and sync events," they noted.

While 99% of companies have data protection solutions in place, 78% of cybersecurity leaders admit they've still had sensitive data breached, leaked, or exposed. "Today, data is highly portable. While AI and cloud technologies are igniting new business ventures that allow employees to connect, create, and collaborate, they also make it easier to leak critical corporate data like source code and IP," said Joe Payne, CEO of Code42.

In Writer, users can enter a ChatGPT-like session to edit or create their documents. In this chat session, the LLM can retrieve information from sources on the web to assist users in creation of their documents.

The advanced persistent threat (APT) actor known as ToddyCat has been linked to a new set of malicious tools that are designed for data exfiltration, offering a deeper insight into the hacking...
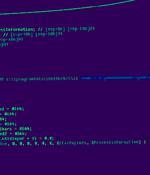
"The attackers aimed to establish a permanent channel for data exfiltration, including data stored on air-gapped systems," Kaspersky said in an analysis spotlighting APT31's previously undocumented tradecraft. Some variants of the second-stage backdoors also come with features designed to look up file names in the Microsoft Outlook folder, execute remote commands, and employ the third-step component to complete the data exfiltration step in the form of RAR archive files.

The report also found that ransomware groups increasingly target the exfiltration of files, the unauthorized extraction or transfer of sensitive information, which has become the primary source of extortion. As these adversaries shift tactics, LockBit has dominated the ransomware landscape, from Q4 2021 to Q2 2023, with 39% of total victims - more than quadruple the number of victims of the second-highest ranked ransomware group.

What we found is an attack scenario that results from chaining security issues found on different Porsche's assets, a website and a GraphQL API, that could lead to data exfiltration. Typically, to be able to perpetrate a CSRF attack from an attacker's-controlled website the victims' web browsers must automatically include the jwtToken cookie in the API requests.