Security News

Threat actors associated with the Vice Society ransomware gang have been observed using a bespoke PowerShell-based tool to fly under the radar and automate the process of exfiltrating data from compromised networks. "Threat actors using built-in data exfiltration methods like negate the need to bring in external tools that might be flagged by security software and/or human-based security detection mechanisms," Palo Alto Networks Unit 42 researcher Ryan Chapman said.

Multi-cloud data storage, once merely a byproduct of the great cloud migration, has now become a strategy for data management. As ransomware attacks continue to rise at a 13% growth rate year over year, surely more cloud storage simply equals more data vulnerability gaps to fill, right? New developments in data technology address these concerns.

The cryptojacking group known as TeamTNT is suspected to be behind a previously undiscovered strain of malware used to mine Monero cryptocurrency on compromised systems. Specifically, the early phase of the attack chain involved the use of a cryptocurrency miner, which the cloud security firm suspected was deployed as a decoy to conceal the detection of data exfiltration.

While massive public data breaches rightfully raise alarms, the spike in malware designed to exfiltrate data directly from devices and browsers is a key contributor to continued user exposure, according to SpyCloud. The 2023 report identified over 22 million unique devices infected by malware last year.

Malicious actors can take advantage of "Insufficient" forensic visibility into Google Cloud Platform to exfiltrate sensitive data, a new research has found. "Unfortunately, GCP does not provide the level of visibility in its storage logs that is needed to allow any effective forensic investigation, making organizations blind to potential data exfiltration attacks," cloud incident response firm Mitiga said in a report.

5 open source Burp Suite penetration testing extensions you should check outWhen it comes to assessing the security of computer systems, penetration testing tools are critical for identifying vulnerabilities that attackers may exploit. LastPass breach: Hacker accessed corporate vault by compromising senior developer's home PCLastPass is, once again, telling customers about a security incident related to the August 2022 breach of its development environment and subsequent unauthorized access to the company's third-party cloud storage service that hosted backups.

Attackers can exfiltrate company data stored in Google Cloud Platform storage buckets without leaving obvious forensic traces of the malicious activity in GCP's storage access logs, Mitiga researchers have discovered. "In normal usage, files inside storage objects are read multiple times a day as part of day-to-day activity of the organization," Mitiga cloud incident responder Veronica Marinov noted.
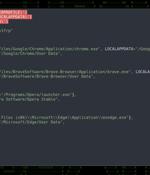
Cybersecurity researchers have unearthed a new Python-based attack campaign that leverages a Python-based remote access trojan to gain control over compromised systems since at least August 2022. LNK files retrieves two text files from a remote server that are subsequently renamed to.

The BlackCat ransomware isn't showing any signs of slowing down, and the latest example of its evolution is a new version of the gang's data exfiltration tool used for double-extortion attacks. BlackCat is considered a successor to Darkside and BlackMatter and is one of the most sophisticated and technically advanced Ransomware-as-a-service operations.

Crypto valuations have dropped, reducing the monetary appeal of ransomware attacks due to organizations mounting a formidable defense against ransomware. Instead, attackers on an information exfiltration mission will move vast amounts of proprietary data to systems that they control.