Security News

Security researchers are seeing an uptick in the use of reverse tunnel services along with URL shorteners for large-scale phishing campaigns, making the malicious activity more difficult to stop. With reverse tunnels, threat actors can host the phishing pages locally on their own computers and route connections through the external service.

The Chinese-backed Hafnium hacking group has been linked to a piece of a new malware that's used to maintain persistence on compromised Windows environments. Microsoft Threat Intelligence Center, which dubbed the defense evasion malware "Tarrask," characterized it as a tool that creates "Hidden" scheduled tasks on the system.

The Palestinian-aligned APT group tracked as TA402 was spotted using a new implant named 'NimbleMamba' in a cyber-espionage campaign that leverages geofencing and URL redirects to legitimate websites. If the target's IP address matches the defined targeted region, a copy of NimbleMamba is dropped on their system inside a RAR file.

Menlo Security announced it has identified a surge in cyberthreats, termed Highly Evasive Adaptive Threats, that bypass traditional security defenses. HEAT attacks are a class of cyber threats targeting web browsers as the attack vector and employs techniques to evade detection by multiple layers in current security stacks including firewalls, Secure Web Gateways, sandbox analysis, URL Reputation, and phishing detection.
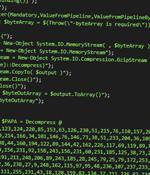
A new, sophisticated phishing attack has been observed delivering the AsyncRAT trojan as part of a malware campaign that's believed to have commenced in September 2021. "Through a simple email phishing tactic with an html attachment, threat attackers are delivering AsyncRAT designed to remotely monitor and control its infected computers through a secure, encrypted connection," Michael Dereviashkin, security researcher at enterprise breach prevention firm Morphisec, said in a report.
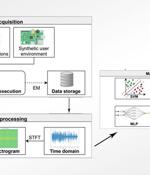
Cybersecurity researchers have proposed a novel approach that leverages electromagnetic field emanations from the Internet of Things devices as a side-channel to glean precise knowledge about the different kinds of malware targeting the embedded systems, even in scenarios where obfuscation techniques have been applied to hinder analysis. With the rapid adoption of IoT appliances presenting an attractive attack surface for threat actors, in part due to them being equipped with higher processing power and capable of running fully functional operating systems, the latest research aims to improve malware analysis to mitigate potential security risks.

Microsoft says that a year-long and highly evasive spear-phishing campaign has targeted Office 365 customers in multiple waves of attacks starting with July 2020. The ongoing phishing campaign lures targets into handing over their Office 365 credentials using invoice-themed XLS.HTML attachments and various information about the potential victims, such as email addresses and company logos.

Cybercrime actors part of the Magecart group have latched on to a new technique of obfuscating the malware code within comment blocks and encoding stolen credit card data into images and other files hosted on the server, once again demonstrating how the attackers are continuously improving their infection chains to escape detection. "One tactic that some Magecart actors employ is the dumping of swiped credit card details into image files on the server [to] avoid raising suspicion," Sucuri Security Analyst, Ben Martin, said in a write-up.

Today’s networks have more sophisticated automated defenses than ever, yet cybercriminals are taking full advantage of business disruptions and distractions in 2020. Adversaries are exploiting...

Scripts can also be used for malicious purposes, and malicious scripts are unlikely to be detected or blocked by the average antimalware solution. While Emotet is one example of threat that uses scripts as part of its evasive strategy, there are many other types of script-based evasion techniques organizations need to be aware of to keep their systems secure.