Security News

An analysis of the "Evasive and tenacious" malware known as QBot has revealed that 25% of its command-and-control servers are merely active for a single day. What's more, 50% of the servers don't remain active for more than a week, indicating the use of an adaptable and dynamic C2 infrastructure, Lumen Black Lotus Labs said in a report shared with The Hacker News.

A 25% increase in the use of phishing kits has been recorded in 2022, according to Group-IB. The key phishing trends observed are the increasing use of access control and advanced detection evasion techniques. The rise in evasive tactics, such as antibot techniques and randomization, poses a significant challenge for conventional detection systems and extends the lifespan of phishing campaigns.
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "In2al5d p3in4er" that's used to deliver the Aurora information stealer malware. "The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM technique," cybersecurity firm Morphisec said in a report shared with The Hacker News.
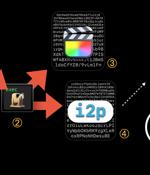
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. "This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.

Cybersecurity researchers have unearthed a new piece of evasive malware dubbed Beep that's designed to fly under the radar and drop additional payloads onto a compromised host. Other instructions the malware is capable of accepting from a command-and-control server include the ability to execute DLL and EXE files.

In this Help Net Security video, Tonia Dudley, VP, CISO at Cofense, provides a look at the various changes seen in the phishing threat landscape. Dudley talks about the impact of credential phishing and business email compromise, which allow cybercriminals to steal substantial amounts of money from global organizations.

Phishing actors are abusing LinkedIn's Smart Link feature to bypass email security products and successfully redirect targeted users to phishing pages that steal payment information.Smart Link is a feature reserved for LinkedIn Sales Navigator and Enterprise users, allowing them to send a pack of up to 15 documents using a single trackable link.

A.NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware as well as targeted payloads like Cobalt Strike and Metasploit, likely since 2015. "DarkTortilla has versatility that similar malware does not," the researchers noted.

Security researchers at Intezer and BlackBerry have documented Symbiote, a wholly unique, multi-purpose piece of Linux malware that is nearly impossible to detect. "What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object library that is loaded into all running processes using LD PRELOAD, and parasitically infects the machine," the researchers pointed out.

Security researchers are seeing an uptick in the use of reverse tunnel services along with URL shorteners for large-scale phishing campaigns, making the malicious activity more difficult to stop. With reverse tunnels, threat actors can host the phishing pages locally on their own computers and route connections through the external service.