Security News

The European Commission on Thursday banned the use of the TikTok short video app on corporate devices and on the personal devices of employees enrolled in the commission's mobile device management service. The commission's statement cites the need to protect staff from a rising number of cyber threats but fails to explain while TikTok was singled out.
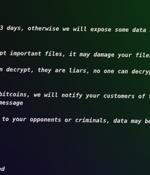
More than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware strain, most of which are located in France, Germany, the Netherlands, the U.K., and Ukraine. Some of the crucial differences between the two ransom notes include the use of an onion URL instead of a Tox chat ID, a Proton Mail address at the bottom of the note, and a lower ransom demand.

Multiple call centers across Europe controlled by a criminal organization involved in online investment fraud were taken down this week following a cross-border investigation started in June 2022. Law enforcement from Bulgaria, Cyprus, Germany, and Serbia found that suspects operating out of these call centers tricked victims into investing large amounts of money in fake cryptocurrency schemes, also known as 'Pig Butchering' cryptocurrency scams.

The China-linked nation-state hacking group referred to as Mustang Panda is using lures related to the ongoing Russo-Ukrainian War to attack entities in Europe and the Asia Pacific. Mustang Panda is a prolific cyber-espionage group from China that's also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.

Review and manage your consent Here's an overview of our use of cookies, similar technologies and how to manage them. The European Parliament has experienced a cyber attack that started not long after it declared Russia to be a state sponsor of terrorism.

North Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and Latin America. In the new campaign, Kaspersky has seen DTrack distributed using filenames commonly associated with legitimate executables.

The Russia-linked APT29 nation-state actor has been found leveraging a "Lesser-known" Windows feature called Credential Roaming as part of its attack against an unnamed European diplomatic entity. "The diplomatic-centric targeting is consistent with Russian strategic priorities as well as historic APT29 targeting," Mandiant researcher Thibault Van Geluwe de Berlaere said in a technical write-up.

The ByteDance-owned platform, which currently stores European user data in the U.S. and Singapore, said the revision is part of its ongoing data governance efforts to limit employee access to users in the region, minimize data flows outside of it, and store the information locally. "Based on a demonstrated need to do their job, subject to a series of robust security controls and approval protocols, and by way of methods that are recognised under the GDPR, we allow certain employees within our corporate group located in Brazil, Canada, China, Israel, Japan, Malaysia, Philippines, Singapore, South Korea, and the U.S. remote access to TikTok European user data," the company said.

Law enforcement authorities in France, in collaboration with Spain and Latvia, have disrupted a cybercrime ring that leveraged a hacking tool to steal cars without having to use a physical key fob. "The criminals targeted vehicles with keyless entry and start systems, exploiting the technology to get into the car and drive away," Europol said in a press statement.

Akamai says it has absorbed the largest-ever publicly known distributed denial of service attack - an assault against an unfortunate Eastern European organization that went beyond 700 million packets per second. For comparison, the July attack peaked at 659.6 Mpps with the organization coming under attack 75 times at its primary data center.