Security News

A relatively new ransomware operation known as Nevada seems to grow its capabilities quickly as security researchers noticed improved functionality for the locker targeting Windows and VMware ESXi systems. Nevada ransomware features a Rust-based locker, real-time negotiation chat portal, separate domains in the Tor network for affiliates and victims.

VMware released security updates to address a critical-severity vulnerability impacting ESXi, Workstation, Fusion, and Cloud Foundation, and a critical-severity command injection flaw affecting vRealize Network Insight.The VMware ESXi heap out-of-bounds write vulnerability is tracked as CVE-2022-31705 and has received a CVSS v3 severity rating of 9.3.

A previously undocumented Python backdoor targeting VMware ESXi servers has been spotted, enabling hackers to execute commands remotely on a compromised system. VMware ESXi is a virtualization platform commonly used in the enterprise to host numerous servers on one device while using CPU and memory resources more effectively.

Over 45,000 VMware ESXi servers inventoried by Lansweeper just reached end-of-life, with VMware no longer providing software and security updates unless companies purchase an extended support contract. As of October 15, 2022, VMware ESXi 6.5 and VMware ESXi 6.7 reached end-of-life and will only receive technical support but no security updates, putting the software at risk of vulnerabilities.
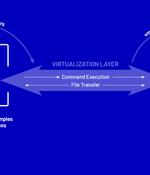
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection. Google's Mandiant threat intelligence division referred to it as a "Novel malware ecosystem" that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.

Hackers have found a new method to establish persistence on VMware ESXi hypervisors to control vCenter servers and virtual machines for Windows and Linux while avoiding detection.A modified level of trust is not enough for the ESXi system to accept it by default but the attacker also used the '-force' flag to install the malicious VIBs.

VMware is warning that ESXi VMs running on Linux kernel 5.19 can have up to a 70% performance drop when Retbleed mitigations are enabled compared to the Linux kernel 5.18 release. More specifically, the VMware performance team noticed regressions on ESXi virtual machines of up to 70% in computing, 30% in networking, and 13% in storage.

A new ransomware family called 'GwisinLocker' targets South Korean healthcare, industrial, and pharmaceutical companies with Windows and Linux encryptors, including support for encrypting VMware ESXi servers and virtual machines. On Wednesday, Korean cybersecurity experts at Ahnlab published a report on the Windows encryptor, and yesterday, security researchers at ReversingLabs published their technical analysis of the Linux version.

Kaspersky security researchers have disclosed details of a brand-new ransomware family written in Rust, making it the third strain after BlackCat and Hive to use the programming language. Luna, as it's called, is "Fairly simple" and can run on Windows, Linux, and ESXi systems, with the malware banking on a combination of Curve25519 and AES for encryption.

A new ransomware family dubbed Luna can be used to encrypt devices running several operating systems, including Windows, Linux, and ESXi systems.Discovered by Kaspersky security researchers via a dark web ransomware forum ad spotted by the company's Darknet Threat Intelligence active monitoring system, Luna ransomware appears to be specifically tailored to be used only by Russian-speaking threat actors.