Security News

A new custom backdoor dubbed Stealth Soldier has been deployed as part of a set of highly-targeted espionage attacks in North Africa. "Stealth Soldier malware is an undocumented backdoor that primarily operates surveillance functions such as file exfiltration, screen and microphone recording, keystroke logging and stealing browser information," cybersecurity company Check Point said in a technical report.

A hacking group tracked as 'Asylum Ambuscade' was observed in recent attacks targeting small to medium-sized companies worldwide, combining cyber espionage with cybercrime. ESET has published a new report on the actor today, disclosing more details about last year's Asylum Ambuscade operations and highlighting updates on its victimology and toolset.
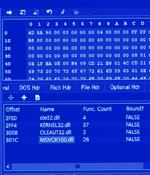
The infamous Lazarus Group actor has been targeting vulnerable versions of Microsoft Internet Information Services servers as an initial breach route to deploy malware on targeted systems. The findings come from the AhnLab Security Emergency response Center, which detailed the advanced persistent threat's continued abuse of DLL side-loading techniques to deploy malware.

The Computer Emergency Response Team of Ukraine has warned of cyber attacks targeting state bodies in the country as part of an espionage campaign. In the attack chain described by the agency, the emails targeted an unspecified ministry and purported to be from the Embassy of Tajikistan in Ukraine.
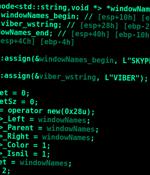
New findings about a hacker group linked to cyber attacks targeting companies in the Russo-Ukrainian conflict area reveal that it may have been around for much longer than previously thought. Bad Magic was first documented by the company in March 2023, detailing the group's use of a backdoor called PowerMagic and a modular framework dubbed CommonMagic in attacks targeting Russian-occupied territories of Ukraine.

The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced malware strain known as Snake wielded by Russia's Federal Security Service. Snake, dubbed the "Most sophisticated cyber espionage tool," is the handiwork of a Russian state-sponsored group called Turla, which the U.S. government attributes to a unit within Center 16 of the FSB. The threat actor has a track record of heavily focusing on entities in Europe, the Commonwealth of Independent States, and countries affiliated with NATO, with recent activity expanding its footprint to incorporate Middle Eastern nations deemed a threat to countries supported by Russia in the region.

Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. "Each of these APTs relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information across the internet," Guy Rosen, chief information security officer at Meta, said.

Hackers are deploying new Linux malware variants in cyberespionage attacks, such as a new PingPull variant and a previously undocumented backdoor tracked as 'Sword2033. PingPull is a RAT first documented by Unit 42 last summer in espionage attacks conducted by the Chinese state-sponsored group Gallium, also known as Alloy Taurus.

The cyber espionage actor tracked as Blind Eagle has been linked to a new multi-stage attack chain that leads to the deployment of the NjRAT remote access trojan on compromised systems. "The group is known for using a variety of sophisticated attack techniques, including custom malware, social engineering tactics, and spear-phishing attacks," ThreatMon said in a Tuesday report.

U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against targets. The activity has been attributed to a threat actor tracked as APT28, which is also known as Fancy Bear, Forest Blizzard, FROZENLAKE, and Sofacy, and is affiliated with the Russian General Staff Main Intelligence Directorate.