Security News

Interview AWS has unveiled MadPot, its previously secret threat-intelligence tool that one of the cloud giant's security execs tells us has thwarted Chinese and Russian spies - and millions of bots. The massive honeypot system has been around since 2010, and includes tens of thousands of threat sensors monitoring criminals' attempts to connect with AWS decoys.

China's Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei's servers, stealing critical data, and implanting backdoors since 2009, amid mounting geopolitical tensions...

A Chinese espionage-focused hacker tracked as 'Earth Lusca' was observed targeting government agencies in multiple countries, using a new Linux backdoor dubbed 'SprySOCKS.'. Trend Micro's analysis of the novel backdoor showed that it originates from the Trochilus open-source Windows malware, with many of its functions ported to work on Linux systems.

NET-based information stealer malware dubbed SapphireStealer is being used by multiple entities to enhance its capabilities and spawn their own bespoke variants. "Information-stealing malware like SapphireStealer can be used to obtain sensitive information, including corporate credentials, which are often resold to other threat actors who leverage the access for additional attacks, including operations related to espionage or ransomware/extortion," Cisco Talos researcher Edmund Brumaghin said in a report shared with The Hacker News.
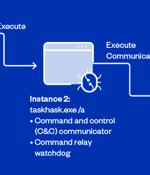
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting government and technology industries based in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S. "The threat actors behind Earth Estries are working with high-level resources and functioning with sophisticated skills and experience in cyber espionage and illicit activities," Trend Micro researchers Ted Lee, Lenart Bermejo, Hara Hiroaki, Leon M Chang, and Gilbert Sison said. Active since at least 2020, Earth Estries is said to share tactical overlaps with another nation-state group tracked as FamousSparrow, which was first exposed by ESET in 2021 as exploiting ProxyLogon flaws in Microsoft Exchange Server to penetrate hospitality, government, engineering, and legal sectors.

PLUS: India calls for global action on AI and crypto; Vietnam seeks cybersecurity independence; China bans AI prescribing drugs Asia In Brief Taiwan-based infosec consultancy Team T5 has disputed...

A nation-state activity group originating from China has been linked to cyber attacks on dozens of organizations in Taiwan as part of a suspected espionage campaign. The Microsoft Threat Intelligence team is tracking the activity under the name Flax Typhoon, which is also known as Ethereal Panda.
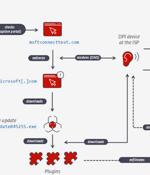
A hitherto undocumented threat actor operating for nearly a decade and codenamed MoustachedBouncer has been attributed to cyber espionage attacks aimed at foreign embassies in Belarus. "To compromise their targets, MoustachedBouncer operators tamper with their victims' internet access, probably at the ISP level, to make Windows believe it's behind a captive portal," Faou said.

The U.S. government on Tuesday added two foreign commercial spyware vendors, Cytrox and Intellexa, to an economic blocklist for weaponizing cyber exploits to gain unauthorized access to devices and "Threatening the privacy and security of individuals and organizations worldwide." Cytrox is the maker of a mobile mercenary spyware called Predator that's analogous to NSO Group's Pegasus.

On June 30 it issued a new one [PDF] titled "US Business Risk: People's Republic of China Laws Expand Beijing's Oversight of Foreign and Domestic Companies." The first item discussed is China's recently revised Counter-Espionage Law, on grounds it "Expands the definition of espionage from covering state secrets and intelligence to any documents, data, materials, or items related to national security interests, without defining terms." In May, China Law Translate - a crowdsourced translation and analysis service for Chinese laws - in May rated the updated law "Probably less consequential than some imagine."