Security News

In this post, we're going to look at some of the ways Material Security's unique approach to email security and data protection can dramatically-and quantifiably-save your security teams hours each week while improving the effectiveness of your security program. Just like your department has a budget that limits how much money you can spend on people and tools, your security teams have a limit to the amount of time they can devote to responding to threats on any given day.

Thousands of email addresses have been compromised after hackers used them to create Google Workspace accounts and bypassed the verification process. One impacted user that shared their experience on a Google Cloud Community forum was notified by Google that someone had created a Workspace account with their email without verification and then used it to log into Dropbox.

A huge phishing campaign exploited a security blind-spot in Proofpoint's email filtering systems to send an average of three million "Perfectly spoofed" messages a day purporting to be from Disney, IBM, Nike, Best Buy, and Coca-Cola - all of which are Proofpoint customers. Guardio dubbed the campaign EchoSpoofing - because the spam was "Echoed" from email relay servers owned and operated by Proofpoint itself.

A massive phishing campaign dubbed "EchoSpoofing" exploited now-fixed, weak permissions in Proofpoint's email protection service to dispatch millions of spoofed emails impersonating big entities like Disney, Nike, IBM, and Coca-Cola, to target Fortune 100 companies. The campaign started in January 2024, disseminating an average of 3 million spoofed emails daily and reaching a peak of 14 million emails in early June.
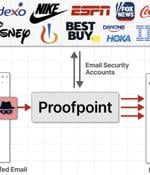
An unknown threat actor has been linked to a massive scam campaign that exploited an email routing misconfiguration in email security vendor Proofpoint's defenses to send millions of messages spoofing various popular companies like Best Buy, IBM, Nike, and Walt Disney, among others. "These emails echoed from official Proofpoint email relays with authenticated SPF and DKIM signatures, thus bypassing major security protections - all to deceive recipients and steal funds and credit card details," Guardio Labs researcher Nati Tal said in a detailed report shared with The Hacker News.

Cisco has fixed two critical vulnerabilities that may allow attackers to overwrite files on its Secure Email Gateways and change the password of any user on its Smart Software Manager On-Prem license servers. Cisco Secure Email Gateways aim to protect businesses against emails laden with malware, malicious links and scams, and against exfiltration of sensitive data via email.

A threat actor has released over 15 million email addresses associated with Trello accounts that were collected using an unsecured API in January. Emo created a list of 500 million email addresses and fed it into the API to determine if they were linked to a Trello account.

Phishing attacks are one of the most common types of data breach attempts, with 31,000 phishing attacks launching every single day, according to cybersecurity firm SlashNext. 77% of cybersecurity professionals report being targeted by phishing attacks, proving just how widespread these attacks are.

A May 2024 data breach disclosed by American luxury retailer and department store chain Neiman Marcus last month has exposed more than 31 million customer email addresses, according to Have I Been Pwned founder Troy Hunt, who analyzed the stolen data. In a separate incident notification published on its website, Neiman Marcus revealed that the data exposed in the attack included names, contact information, dates of birth, gift card info, transaction data, partial credit card and Social Security numbers, and employee identification numbers.

FIA, the auto racing governing body since the 1950s, says attackers gained access to personal data after compromising several FIA email accounts in a phishing attack. Founded in 1904 as the Association Internationale des Automobile Clubs Reconnus, FIA is a non-profit international association that coordinates many auto racing championships, including Formula 1 and the World Rally Championship.