Security News

Toyota Tsusho Insurance Broker India, an Indo-Japanese joint insurance venture, operated a misconfigured server that exposed more than 650,000 Microsoft-hosted email messages to customers, a security researcher has found. Zveare then examined the calculator web page on the TTIBI website and saw that it included a client-side function that created a request to send email using a server-side API. "This caught my eye because this was a client-side email sending mechanism," he wrote in a post describing his findings.

Have I Been Pwned has added almost 71 million email addresses associated with stolen accounts in the Naz.API dataset to its data breach notification service. The Naz.API dataset is a massive collection of 1 billion credentials compiled using credential stuffing lists and data stolen by information-stealing malware.

A Chinese state-backed research institute claims to have discovered how to decrypt device logs for Apple's AirDrop feature, allowing the government to identify phone numbers or email addresses of those who shared content. China has a long history of censoring its people, requesting Apple block access to mobile apps, blocking encrypted messaging apps, such as Signal, and creating the Great Firewall of China to control what sites can be visited in the country.

Email-based attacks have evolved beyond traditional spam and phishing attempts. Email attacks can result in financial losses, reputational damage, and the compromise of sensitive information.
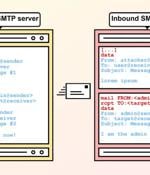
A new exploitation technique called Simple Mail Transfer Protocol (SMTP) smuggling can be weaponized by threat actors to send spoofed emails with fake sender addresses while bypassing security...

Integris Health patients in Oklahoma are receiving blackmail emails stating that their data was stolen in a cyberattack on the healthcare network, and if they did not pay an extortion demand, the data would be sold to other threat actors. "INTEGRIS Health discovered potential unauthorized activity on certain systems," reads a data privacy notice on Integris Health's website.

The Israel National Cyber Directorate warns of phishing emails pretending to be F5 BIG-IP zero-day security updates that deploy Windows and Linux data wipers. In November, a new data wiper called BiBi Wiper was discovered that targeted both Linux and Windows devices and is believed to have been created by pro-Hamas hacktivists.

Cybercriminals are preying on the inherent helpfulness of hotel staff during the sector's busy holiday season. When the staff then responds by requesting more information, the attacker sends a message directing the staff to open a link that supposedly contains evidence supporting their claim.

Microsoft has taken down US-based infrastructure and websites used by a cybercrime group to sell fraudulent online accounts to other crooks including Scattered Spider, the infamous social-engineering and extortion crew that hacked two Las Vegas casinos over the summer. The gang, Storm-1152, is the "Number one seller and creator of fraudulent Microsoft accounts" and has listed for sale 750 million of these, according to Amy Hogan-Burney, Microsoft's associate general counsel for cybersecurity policy and protection.

Karakurt, a particularly nasty extortion gang that uses "Extensive harassment" to pressure victims into handing over millions of dollars in ransom payments after compromising their IT infrastructure, pose a "Significant challenge" for network defenders, we're told. So to help organizations avoid getting caught by this crew, the FBI, and the US government's Cybersecurity and Infrastructure Security Agency, Treasury Department, and Financial Crimes Enforcement Network released an extensive list of vulnerabilities and methods the gang exploits and uses for initial access, the software tools they abuse to snoop around and steal data, and the payment wallets and even email addresses used in the group's extortion attacks.