Security News

SafeBreach researchers have discovered eight new process injection techniques that can be used to covertly execute malicious code on Windows systems. Dubbed "Pool Party" because theyuse Windows thread pools, these process injection techniques work across all processes and, according to the researchers, they went undetected when tested against five leading EDR/XDR solutions, namely: Palo Alto Cortex, SentinelOne EDR, CrowdStrike Falcon, Microsoft Defender For Endpoint, and Cybereason EDR. "Pool Party" process injection techniques.
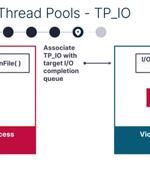
A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response...

Emsisoft is having a holiday deal where you can get 20% off 1-year licenses of the Emsisoft Enterprise Security EDR solution through December 17th, 2023, with no license limits. Emsisoft's Enterprise Security provides a cloud-based management console where you can see an overview of all your endpoints and any security incidents that need to be investigated, whether malware or other anomalous behavior.

Best EDR Of The Market is a user-mode endpoint detection and response project designed to serve as a testing ground for understanding and bypassing EDR's user-mode detection methods. These techniques are mainly based on a dynamic analysis of the target process state,.

An updated version of the MATA backdoor framework was spotted in attacks between August 2022 and May 2023, targeting oil and gas firms and the defense industry in Eastern Europe. The updated MATA framework combines a loader, a main trojan, and an infostealer to backdoor and gain persistence in targeted networks.

A new process injection technique named 'Mockingjay' could allow threat actors to bypass EDR and other security products to stealthily execute malicious code on compromised systems. Process injection is a method of executing arbitrary code in the address space of another running process that is trusted by the operating system, hence giving threat actors the ability to run malicious code without being detected.

The Windows 11 22H2 KB5027231 cumulative update released during this month's Patch Tuesday also breaks Google Chrome on systems protected by Cisco and WatchGuard EDR and antivirus solutions. As BleepingComputer reported on Wednesday, Windows admins and users report having issues launching the web browser after installing the KB5027231 Windows 11 updates.
Threat actors are employing a previously undocumented "Defense evasion tool" dubbed AuKill that's designed to disable endpoint detection and response software by means of a Bring Your Own Vulnerable Driver attack. "The AuKill tool abuses an outdated version of the driver used by version 16.32 of the Microsoft utility, Process Explorer, to disable EDR processes before deploying either a backdoor or ransomware on the target system," Sophos researcher Andreas Klopsch said in a report published last week.
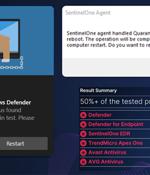
EDR software, by design, are capable of continually scanning a machine for potentially suspicious and malicious files, and taking appropriate action, such as deleting or quarantining them. The idea, in a nutshell, is to trick vulnerable security products into deleting legitimate files and directories on the system and render the machine inoperable by making use of specially crafted paths.

A security researcher has found a way to exploit the data deletion capabilities of widely used endpoint detection and response (EDR) and antivirus (AV) software from Microsoft, SentinelOne,...