Security News

Virtual Chief Information Security Officer (vCISO) services are in high demand. Even though it is clear to all that this trend is growing, most service providers only offer a portion of overall...

As cyberattacks escalate, more regulations are being introduced to help protect organizations and their customers’ data. This has resulted in a complex web of legislation with which companies in...

Organizations sometimes need to plan their cloud migrations with more emphasis on security and compliance. Many, therefore, struggle to keep their data safe after migrating to the cloud. To...

More organizations rely on cloud platforms to reap the benefits of scalability, flexibility, availability, and reduced costs. However, cloud environments come with security challenges and...

CISSP carries clout. As the world’s leading cybersecurity certification, it opens many professional opportunities worldwide. Find out what led 14 successful CISSPs around the globe to a career in...
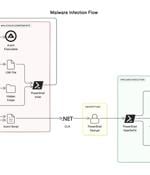
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations," Trellix security researchers Mathanraj Thangaraju and Sijo Jacob said.

Please turn on your JavaScript for this page to function normally. Password security has seen dramatic shifts driven by the escalation of cyber threats and technological advancements.

Software security requires a creative and disciplined approach. It involves having the vision to develop secure strategy, tactics, and execution. Excelling in the discipline demands thinking...

There’s never been a better time to deepen your skills in cybersecurity as the demand for experienced experts continues to grow. Learn how to break today’s bad actors in the eBook. Inside the...

Current demand for cloud security specialists far exceeds available talent. Especially for companies seeking protection in multicloud environments, professionals with vendor-neutral knowledge and...