Security News

You can now connect your Box and Dropbox accounts to Deep Research on ChatGPT and pull data, which will be used by the AI to conduct research. [...]
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed...

Cloud storage services provider Dropbox on Wednesday disclosed that Dropbox Sign (formerly HelloSign) was breached by unidentified threat actors, who accessed emails, usernames, and general...

File hosting service Dropbox has confirmed that attackers have breached the Dropbox Sign production environment and accessed customer personal and authentication information. "Based on our investigation, a third party gained access to a Dropbox Sign automated system configuration tool. The actor compromised a service account that was part of Sign's back-end, which is a type of non-human account used to execute applications and run automated services. As such, this account had privileges to take a variety of actions within Sign's production environment."

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Cloud storage firm DropBox says hackers breached production systems for its DropBox Sign eSignature platform and gained access to authentication tokens, MFA keys, hashed passwords, and customer information.DropBox Sign is an eSignature platform allowing customers to send documents online to receive legally binding signatures.

There's a rumor flying around the Internet that OpenAI is training foundation models on your Dropbox documents. Dropbox isn't sharing all of your documents with OpenAI. But here's the problem: we don't trust OpenAI. We don't trust tech corporations.
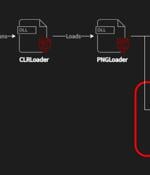
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor's infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that's used to facilitate information theft.

Dropbox has suffered a data breach, but users needn't worry because the attackers did not gain access to anyone's Dropbox account, password, or payment information. The compromised repositories contain "Copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the security team" - but not code for Dropbox core apps or infrastructure.

File hosting service Dropbox on Tuesday disclosed that it was the victim of a phishing campaign that allowed unidentified threat actors to gain unauthorized access to 130 of its source code repositories on GitHub."These repositories included our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and configuration files used by the security team," the company revealed in an advisory.