Security News

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two six-year-old security flaws impacting Sitecore CMS and Experience Platform (XP) to its Known Exploited...

Time to update your firmware, if you can, to one with the security fixes, cough cough DrayTek router owners in the UK and beyond had a pretty miserable weekend after some ISPs began to notice a...

Many Internet service providers (ISPs) worldwide are alerting customers of an outage that started Saturday night and triggered DrayTek router connectivity problems. [...]

With 14 serious security flaws found, what a gift for spies and crooks Fourteen bugs in DrayTek routers — including one critical remote-code-execution flaw that received a perfect 10 out of 10...

A little over a dozen new security vulnerabilities have been discovered in residential and enterprise routers manufactured by DrayTek that could be exploited to take over susceptible devices....

DrayTek has released security updates for multiple router models to address 14 vulnerabilities of varying severity, including a remote code execution flaw that received the maximum CVSS score of 10. [...]
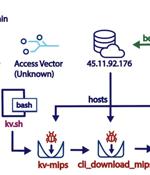
A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used as a covert data transfer network for advanced persistent threat actors, including the...

If you're still running post-support DrayTek Vigor routers it may be time to junk them, or come up with some other workaround, as a cunning malware variant is setting up shop in the kit. The operators behind the Hiatus malware campaign are hijacking DrayTek Vigor router models 2960 and 3900 powered by MIPS, i386 and Arm-based processors to in turn attack businesses in North and Latin America as well as in Europe, according to researchers with Lumen's Black Lotus Labs threat intelligence unit.

An ongoing hacking campaign called 'Hiatus' targets DrayTek Vigor router models 2960 and 3900 to steal data from victims and build a covert proxy network. DrayTek Vigor devices are business-class VPN routers used by small to medium-size organizations for remote connectivity to corporate networks.

As many as 29 different router models from DrayTek have been identified as affected by a new critical, unauthenticated, remote code execution vulnerability that, if successfully exploited, could lead to full compromise of the device and unauthorized access to the broader network. Over 200,000 devices from the Taiwanese manufacturer are said to have the vulnerable service currently exposed on the internet and would require no user interaction to be exploited.