Security News

NET-based DNS backdoor to conduct attacks on companies in the energy and telecommunication sectors. A recent analysis by Zscaler presents a new DNS backdoor based on the DIG.net open-source tool to carry out "DNS hijacking" attacks, execute commands, drop more payloads, and exfiltrate data.

EfficientIP has announced the findings of its eighth annual 2022 Global DNS Threat Report, conducted by IDC, which reveals the damaging impact Domain Name System attacks have had on global organizations' operations over the past 12 months. As enterprises continue to strike a balance between supporting remote workers and mitigating the network security risks posed by the rise in hybrid work models and reliance on cloud applications, the results show that 88% of organizations have experienced one or more DNS attacks on their business.

An unpatched Domain Name System bug in a popular standard C library can allow attackers to mount DNS poisoning attacks against millions of IoT devices and routers to potentially take control of them, researchers have found. "The flaw is caused by the predictability of transaction IDs included in the DNS requests generated by the library, which may allow attackers to perform DNS poisoning attacks against the target device," Nozomi's Giannis Tsaraias and Andrea Palanca wrote in the post.
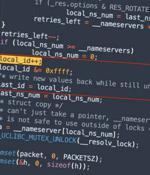
Cybersecurity researchers have disclosed an unpatched security vulnerability that could pose a serious risk to IoT products. The issue, which was originally reported in September 2021, affects the Domain Name System implementation of two popular C libraries called uClibc and uClibc-ng that are used for developing embedded Linux systems.

Microsoft has addressed a new known issue causing DNS stub zones loading failures that could lead to DNS resolution issues on Windows Server 2019 systems. DNS stub zones are copies of DNS zones containing resource records needed to determine the authoritative DNS servers for a specific zone and resolve names between separate DNS namespaces.
First observed propagating through the Log4j vulnerability on February 9, 2022, the malware leverages a technique called DNS tunneling to build communication channels with command-and-control servers by encoding data in DNS queries and responses. B1txor20, while also buggy in some ways, currently supports the ability to obtain a shell, execute arbitrary commands, install a rootkit, open a SOCKS5 proxy, and functions to upload sensitive information back to the C2 server.

The newly found malware, dubbed B1txor20 by researchers at Qihoo 360's Network Security Research Lab, focuses its attacks on Linux ARM, X64 CPU architecture devices. The botnet uses exploits targeting the Log4J vulnerability to infect new hosts, a very appealing attack vector seeing that dozens of vendors use the vulnerable Apache Log4j logging library.

Customers are increasingly turning away from private DNS resolvers and going for large cloud-based public DNS resolvers instead. What are the security concerns driving customers to public DNS resolvers? Better security and privacy are identified as key drivers for this shift to public DNS resolvers.

Providing public Wi-Fi is a great service to offer your customers as it becomes more and more standard in today's society. According to recent statistics, there are about 410,000 public Wi-Fi hotspots in the United States alone, in public places such as parks, libraries, public transportation, and train stations.

Researchers have demonstrated yet another variant of the SAD DNS cache poisoning attack that leaves about 38% of the domain name resolvers vulnerable, enabling attackers to redirect traffic originally destined to legitimate websites to a server under their control. From Kaminsky Attack to SAD DNS. DNS cache poisoning, also called DNS spoofing, is a technique in which corrupt data is introduced into a DNS resolver's cache, so that DNS queries return an incorrect response for a trusted domain and users are directed to malicious websites.