Security News

Intel this month published an advisory to address a novel Spectre v2 vulnerability in its processors that can be exploited by malware to steal data from memory that should otherwise be off limits. Spectre is one of two closely related chip architecture blunders, details of which emerged in 2018; the other being Meltdown that The Register first highlighted.

Rostec, a Russian state-owned aerospace and defense conglomerate, said its website was taken down today following what it described as a "Cyberattack." Rostec claims the website was brought back online quickly and attributed the attack to Ukrainian "Radicals."

Department of Defense contractors struggling to comply with upcoming cybersecurity regulations under the Cybersecurity Maturity Model Certification can breathe a sigh of relief-the DoD has announced its intent to release CMMC 2.0, with promises to streamline the certification process and ease security regulations for contractors and sub-contractors handling low-priority information. Intended to promote compliance with DoD cybersecurity procedures and give teeth to enforcement, the CMMC program was first announced in 2020 to regulate the control of unclassified information and high-value assets by external contractors.
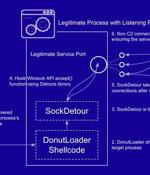
Cybersecurity researchers have taken the wraps off a previously undocumented and stealthy custom malware called SockDetour that targeted U.S.-based defense contractors with the goal of being used as a secondary implant on compromised Windows hosts. "SockDetour is a backdoor that is designed to remain stealthily on compromised Windows servers so that it can serve as a backup backdoor in case the primary one fails," Palo Alto Networks' Unit 41 threat intelligence said in a report published Thursday.

Ransomware is getting worse, but Daniel Spicer, chief security officer at Ivanti, offers a checklist for choosing defense solutions to meet the challenge. Invest in an automated platform that enhances visibility into all connected devices and software and provides context into how those assets are being used, so your IT and security teams can make better decisions.

A new custom malware dubbed SockDetour found on systems belonging to US defense contractors has been used as a backup backdoor to maintain access to compromised networks. SockDetour [.] serves as a backup backdoor in case the primary backdoor is detected and removed by defenders," Unit 42 explained.

A newly discovered custom malware dubbed SockDetour has been found on systems belonging to US defense contractors and used as a backup backdoor to maintain access to compromised networks. SockDetour [.] serves as a backup backdoor in case the primary backdoor is detected and removed by defenders," Unit 42 explained.

These days, information technology and information security professionals know this all too well, especially when it comes to configuration assessments. To reduce opportunities for hackers, organizations should perform configuration assessments regularly.

Microsoft has some advice on how to defend against "Ice phishing" and other novel attacks that aim to empty cryptocurrency wallets, for those not already abstaining. Ice phishing, as Microsoft describes it, is a clickjacking, or a user interface redress attack, that "[tricks] a user into signing a transaction that delegates approval of the user's tokens to the attacker.

State-sponsored actors backed by the Russian government regularly targeted the networks of several U.S. cleared defense contractors to acquire proprietary documents and other confidential information pertaining to the country's defense and intelligence programs and capabilities. Compromised entities include contractors that dabble in command, control, communications, and combat systems; surveillance and reconnaissance; weapons and missile development; vehicle and aircraft design; and software development, data analytics, and logistics.